
The Critical Incident Technique: Method or Methodology?
Chat with Paper
Handbook of Health Research Methods: Investigation, Measurement and Analysis
General practitioners' experiences during the first phase of the covid-19 pandemic in italy: a critical incident technique study., why medical residents do (and don't) speak up about organizational barriers and opportunities to improve the quality of care., health care workers' experiences of workplace incidents that posed a risk of patient and worker injury: a critical incident technique analysis., social justice pedagogies in school health and physical education-building relationships, teaching for social cohesion and addressing social inequities., preventable anesthesia mishaps: a study of human factors, developing flanagan's critical incident technique to elicit indicators of high and low quality nursing care from patients and their nurses., the reliability and validity of the critical incident technique: a closer look., research for health., related papers (5), critical methodology analysis of an article, a critical assessment of quantitative methodology as a policy analysis tool, quality control in qualitative research, case study research in information technology: a prescriptive methodology, service quality models: a review, trending questions (2).
The Critical Incident Technique (CIT) is a methodology, not just a method, due to its distinct focus, use of various data collection and analysis methods, and underlying philosophical assumptions.
The Critical Incident Technique can be applied in focus groups by utilizing various methods for data collection and analysis, focusing on specific incidents to explore care quality.
The Critical Incident Technique in UX

January 26, 2020 2020-01-26
- Email article
- Share on LinkedIn
- Share on Twitter
The critical incident technique (CIT) is a systematic procedure for obtaining rich, qualitative information about significant incidents from observers with firsthand experience, which in turn helps researchers understand the critical requirements for individuals, processes or systems.
The critical incident technique (CIT) is a research method in which the research participant is asked to recall and describe a time when a behavior, action, or occurrence impacted (either positively or negatively) a specified outcome (for example, the accomplishment of a given task).
The instance reported by the participant is known as an ‘incident’. In order for the incident to be critical, the participant must be confident that the event had a causal relationship with the outcome (which is the focus of the study). An example of a critical incident question is given below:
Please think of an Agile project that you worked on that was successful. Please describe a specific time when someone did something (or something happened) that positively contributed to the success of that project.
This method was formally introduced to the social sciences by John Flanagan, in a seminal paper published in the Psychological Bulletin in 1954. The technique was developed and finessed in numerous studies undertaken by Flanagan and fellow psychologists from the US Aviation Psychology Program during the second World War, and later by the American Institute for Research and the University of Pittsburgh. Since the publication of Flanagan’s paper, the CIT has become popular in the social sciences and has found applications in human–computer interaction research, because it facilitates the gathering of many detailed ‘incidents’ (behaviors or events). These are useful in understanding critical requirements for roles, systems, and processes. For example, the CIT has been used to highlight characteristics of successful personnel (such as leaders, nurses, doctors, air-traffic controllers), as well as critical requirements for processes (such as training programs and services) and interfaces.
In UX, the CIT is often used in user interviews . However, critical incidents can also be captured using questionnaires, focus groups , or structured diary studies . Flanagan believed that researchers carrying out ethnographic-style research could also document critical incidents, although little has been said on how this approach should be implemented.
Using the critical incident technique is slightly different from asking a standard, example-style question in a user interview. The table below shows some questions that could be given to employees to learn about their experience using an enterprise tool. A critical incident question is compared to other example-style questions.
| The participant is asked: | Type of question |
|---|---|
| the participant is asked to provide an example; there is no direction from the researcher as to what kind of example. The answer could be anything that happened to come to the participant’s mind. | |
| The participant is asked to describe the most recent time. This is not necessarily a critical incident, just the most recent. | |
| the participant is asked to think of a specific incident that was critical to the accomplishment of a task. |
Usually, in a critical incident interview, the participant is given time to think of each incident before describing it, as recall can often take time. The interviewer also has carefully scripted followup questions meant to elicit enough factual information about the incident. The interview could look something like this:
| Interviewer introduces the focus of the study | |
| Check tool-use criteria | |
| Critical incidents (positive) | |
| Clarification questions | |
| Seek out further incidents | |
| Critical incidents (negative) | |
| Clarification questions | |
| Seek out further incidents |
Generally speaking, when the researcher seeks critical incidents, the participant is asked for events that demonstrate both positive and negative effects on the outcome. These questions are usually separate, as in the example interview above. However, in some cases, the researcher may ask for a positive or negative case at the same time and allow the participant to choose which incident to begin with. When asked separately, it is typical to begin with asking for positive incidents in order to begin constructively.
When the critical incident technique is used in research, each participant could contribute many incidents. It is quite possible that hundreds of incidents (sometimes thousands) are collected through numerous interviews which then need to be coded . When codes are well saturated (e.g., there are many incidents for each code), researchers can be fairly confident that they have documented the core requirements for the object of study. In the enterprise-tool example, these requirements could include ease of access (users need to be able to find and open the tool quickly), responsiveness (the tool needs to respond quickly — for example, autosave shouldn’t slow users down), or nonintrusive updates (updates should not interrupt the user at work).
In This Article:
Pros and cons of using the critical incident technique.
This method has some advantages, as well as some key disadvantages for usability research.
- Quickly uncovers system issues
- Captures incidents over a long timeframe: Participants can go back as long as they can remember. As a result, incidents could span years. This is an advantage over observational research, which is often time restricted.
- Captures information about rare or uncommon incidents: When observing users in their domain, key incidents are not always witnessed because they are rare or uncommon. The CIT makes discovery of these incidents possible.
- Emphasis on more-important issues rather than less-important issues. Most other methods usually collect a preponderance of low-importance issues, simply because they tend to be more numerous. Of course, there’s no guarantee every reported critical incident is actually important, but significant events will likely be easier to recall than minor incidents.
- Flexible : The CIT can be applied in interviews, focus groups, and surveys.
- Relies on memory and pure recall: Memory is fallible, and so details can often be lost, or critical incidents can be forgotten. Recall is also challenging and even stressful for some participants, particularly in a face-to-face setting.
- Doesn’t represent typical usage: Often, participants recall extreme events, but small usability issues and typical usage are rarely mentioned in CIT interviews.
When deciding whether to use the critical incident technique, consider what your research goal is and whether a usability test or observation in the field will be better suited for achieving it. If using the critical incident technique in your research, ensure that you know what type of incidents you want to learn about. Take the time to compose an interview script and pilot it to check that your questions aren’t too prescriptive, vague, or ambiguous. (Anecdotally, researchers have found that varying the types of words used in the critical incident question can affect the type of incidents recalled, so think carefully on how not to lead participants ). Lastly, you will always learn more about how people use existing interfaces and what their pain points are if you carry out observational research, such as contextual inquiry or usability testing .
The critical incident technique (CIT) is a useful methodology to uncover critical requirements for people, systems, and processes. When using the CIT, ensure that you are clear on the kind of incidents you want to study, prepare an interview script, and pilot it. Complement CIT interviews, focus groups, or surveys with observational research (like contextual inquiry and usability tests) to get an accurate picture of the usability of systems, products, or services.
Flanagan, J.C. (1954). The Critical Incident Technique. Psychological Bulletin , 51(4), 327-357.
Related Courses
User interviews.
Uncover in-depth, accurate insights about your users
User Research Methods: From Strategy to Requirements to Design
Pick the best UX research method for each stage in the design process
Discovery: Building the Right Thing
Conduct successful discovery phases to ensure you build the best solution
Related Topics
- Research Methods Research Methods
Learn More:

Competitive Reviews vs. Competitive Research
Therese Fessenden · 4 min

15 User Research Methods to Know Beyond Usability Testing
Samhita Tankala · 3 min

Always Pilot Test User Research Studies
Kim Flaherty · 3 min
Related Articles:
Open-Ended vs. Closed Questions in User Research
Maria Rosala · 5 min
UX Research Methods: Glossary
Raluca Budiu · 12 min
Cognitive Mapping in User Research
Sarah Gibbons · 16 min
Formative vs. Summative Evaluations
Alita Joyce · 5 min
Iterative Design of a Survey Question: A Case Study
Feifei Liu · 8 min
When to Use Which User-Experience Research Methods
Christian Rohrer · 9 min
The Critical Incident Technique: An Innovative Qualitative Method of Research
- Lorette K Woolsey
How to Cite
- Endnote/Zotero/Mendeley (RIS)
Developed By
Subscription.
Login to access subscriber-only resources.
- Français (Canada)
Information
- For Readers
- For Authors
- For Librarians

- Marketing Mix Strategy
- Five Forces
- Business Lists
- Competitors
- Business Concepts
- Human Resources (HR)
Critical Incident Method
This article covers meaning, importance, steps & example of Critical Incident Method from HRM perspective.
What is Critical Incident Method?
Critical incident method or critical incident technique is a performance appraisal tool in which analyses the behavior of employee in certain events in which either he performed very well and the ones in which he could have done better. Critical incident technique is used to collect data using a set of procedures. In critical incident method the observer observes critical human behaviors, skills used, incidents that occur on the job.
In Critical incident method, the manager of the employee gives all the details of the incident. This method is quite subjective in nature as compared to other methods which may be very objective and would require just ratings out of 5/10 etc. It helps to define the competencies and Knowledge, Skills, Abilities and other attributes (KSAO) required for a task or set of tasks that entails a job. The observer not only looks at the hard skills used but also the mental abilities that are required by the job incumbent.
Importance of Critical Incident Technique
Critical Incident Technique is very helpful while making a Job Specification and Job Description. The respondents, usually the job incumbents are asked to tell a story about the experiences they had while performing the job, the interviewer notes down the necessary incidents, skills, mental abilities, knowledge and other attributes that were used during the job by the job incumbent. Critical incident technique is very important and helpful technique to create a Job description and a job specification for a job. Providing a job description and job specification is essential to attract the right candidates for the job and can help to cut down the turnaround time for filling up a vacancy in the organization.
Critical Incident technique notes down the important skills, knowledge, mental abilities and other attributes that are required in the job. Critical Incident Appraisal is used as a performance appraisal process method for employees.
Critical Incident Method Steps
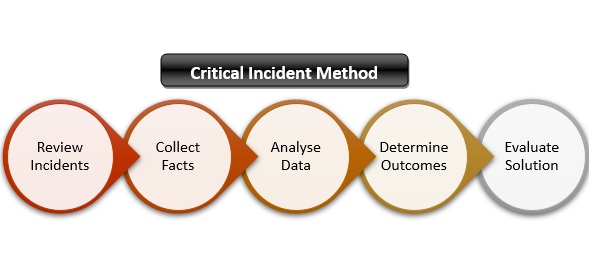
Critical incident technique has the following steps.
1. We start with determining and reviewing the incidents that have taken place during the course of the job
2. Fact finding which involves gathering information of the incident from the members.
3. The third step is to analyze the facts and the data collected by the interviewer from the participants and determine the issues
4. The fourth step is to determine possible solutions for the issues that have been identified
5. Finally the last step is to evaluate whether the solution will be able to remove the cause of the problem that was identified.
Advantages of Critical Incident Technique
A few advantages of critical incident method are:
1. Helps to identify rare events which might be missed by other methods as they focus only on common events.
2. The technique is cost effective and provides rich information
3. The respondent’s perspective is taken into account
4. The respondents are not forced into any framework
5. Many ways to implement the technique like observation, questionnaires and interviews
Disadvantages of Critical Incident Technique
1. Many incidents may go unreported or might not be precise as the reporting of incidents relies on memory of the respondent.
2. Biasness might creep in towards the incidents that happened recently.
3. The incidents narrated may not be representative of everyday situation that takes place during the job.
Example of Critical Incident Method
A few examples are:
1. Critical Incident Technique is a technique to help find facts about a job. Example of critical incidents technique is an interview being taken of the incumbent of the job to know the facts of the job. These facts are collected by various techniques like questionnaires and survey as well and can be used for organizational development and market research. The interviewer should try to extract data related to description and outcome of the critical incident, the feelings, perceptions and thoughts that the person had at the time of the incident. The actions that were taken during the incident and what changes should be undertaken next time this incident takes place.
2. On a particular day one Salesperson stayed 60 minutes beyond his break during the busiest part of the day. Whereas another salesperson fails to answer store manager’s call thrice.
Hence, this concludes the definition of Critical Incident Method along with its overview.
This article has been researched & authored by the Business Concepts Team which comprises of MBA students, management professionals, and industry experts. It has been reviewed & published by the MBA Skool Team . The content on MBA Skool has been created for educational & academic purpose only.
Browse the definition and meaning of more similar terms. The Management Dictionary covers over 1800 business concepts from 5 categories.
Continue Reading:
- Job Description
- Compensation and Benefits
- Career Development
- 360 Degree Feedback
- Employee Training
- Marketing & Strategy Terms
- Human Resources (HR) Terms
- Operations & SCM Terms
- IT & Systems Terms
- Statistics Terms
What is MBA Skool? About Us
MBA Skool is a Knowledge Resource for Management Students, Aspirants & Professionals.
Business Courses
- Operations & SCM
- Human Resources
Quizzes & Skills
- Management Quizzes
- Skills Tests
Quizzes test your expertise in business and Skill tests evaluate your management traits
Related Content
- Marketing Strategy
- Inventory Costs
- Sales Quota
- Quality Control
- Training and Development
- Capacity Management
- Work Life Balance
- More Definitions
All Business Sections
- SWOT Analysis
- Marketing Mix & Strategy
- PESTLE Analysis
- Five Forces Analysis
- Top Brand Lists
Write for Us
- Submit Content
- Privacy Policy
- Contribute Content
- Web Stories

What is Critical Incident Technique?
Critical incident technique advantages and disadvantages, critical incident technique steps, example of critical incident technique, faq for critical incident method, critical incident technique: method, example, steps [guide].
16 Feb 2021
Last updated:

Bluein Christian

Researching an incident and its outcomes to obtain qualitative information is termed as critical incident technique.
In the research, the participants are asked to share their first-hand experience about the behavior, occurrence of a particular situation, and its outcomes.
John Flanagan introduced the method in 1954 through the Psychological Bulletin. The Critical Incident technique is often used in user interviews. While using user interviews, the types of questions asked are slightly different from the method used in the critical incident technique.
Let us take an example to understand the Critical Incident Technique clearly:
Situation: The participant is being asked about a tool that she has used.
- Describe the time when you used the tool- Normal Question
- Describe the time when you used the tool last- Specific Question
- Describe the time when you use the tool for your work, and it helped in making your job easier.- Critical Incident Question
The Critical Incident Technique entails a lot of follow-up questions. For example, the follow-up questions of the above question would be:
- When have you used the tool last?
- How did you use the tool?
- What are the things you do with the tool?
- Why did you choose this particular tool?
The participant is usually asked for both positive and negative feedback. The questions can be asked together or separately. Generally, if the positive and negative questions are asked together, the participant answers the positive questions first.
One participant can give many incidents. Hundreds and even thousands of incidents are collected with the help of many such interviews. When the codes (having the incidents) are saturated, it can be understood that the documentation required to fulfill the criteria is met.
Research paper on Critical Incident Technique by John C Flanagan .
Critical incident technique like all methods has some advantages and disadvantages.
The advantages can be listed as
- If Critical Incident Technique is used, it reveals the errors and issues fast.
- There is no timeframe for taking incidents. The participant can take how much time he wants to evaluate and answer questions.
- If there is some information that is uncommon and rare and cannot be found easily with standard sets of questions, CIT can very effectively evaluate and analyze them.
- CIT gives more importance to the more critical errors and issues.
- CIT is very flexible and can be applied in focus groups and surveys as well as general interviews.
The disadvantages of the method are
- CIT is dependent on human memory; Therefore, if a participant forgets a part of the Incident or interprets it in the wrong way, the process can get stressful and time-consuming.
- Most often, participants give details of monumental events but forget to mention smaller intricate details.
- It is up to the researcher to decide whether or not to use CIT based on the process’s goal. He can also use other tools like usability test if that caters more to his needs.
How to ask the right questions
The steps that can be followed for asking the right questions are:
- Looking for the right person (preferably an expert) from the particular department.
Example of the question to the expert: If a new person for the role of Manager is being hired, what roles would he be expected to fulfill or how many hours would he be expected to work a day?
Then there are questions which are built specifically for a particular situation. The example of questions concerning the event that happened could be like:
- Where did it occur?
- How did it occur?
- What was done after it happened?
2. Ask for the solution like what works, what does not work, and what might be useful for future situations. This helps in understanding what should be done and what should not be done.
3. Repeat the same steps with other divisional heads to evaluate whether or not the desired result is achieved. If the same method is applied for various heads, different perspectives on the same work are found.
4. Evaluate the situations and make questions out of them and the examples to analyze the behavior.
- Good answers
- Mediocre answers
- Bad answers
More information about Critical Incident Technique
The steps of the Critical Incident Technique are as follows:
- The situation is reviewed and has to be analyzed.
- Collect the facts from the incidents for analysis.
- Analyze the data that has been collected.
- The results are determined.
- Evaluate the results.
If for example Critical Incident Technique was used to find information about a particular job it would be like: the information about the job is taken by various ways like questionnaires. These surveys can be used for market research.
The participant is asked about his feeling and perspectives of the Incident. The actions were taken during the situation, how the activities altered the situation and what can be done to better it. He is asked about the description of the roles that the job entails. He is intricately asked about details.
The little information that might be missed by tools like user interviews can be extracted by Critical Incident Technique. The job description is evaluated when the participant describes various incidents and his feelings towards those incidents. Usually, more than one participant is used to see different perspectives of the same situation.
What is a critical incident method in a personal appraisal?
Critical incident method in the personal appraisal is a tool used to measure the performance of the employee in many mobile app development companies and other too. The performances can be outstanding, or they can be asked to be made better.
What is a Critical Incident?
Critical Incident can be defined as the exact moment when the Incident happens and its effectiveness.
When was the Critical Incident Method used, and for what purpose?
Critical Incident Method was developed in 1954 to aid the US Air Force Pilots during World War 2 to understand why certain pilots were selected, classified, and evaluated.
What is an example of a Critical Incident?
Critical Incident Technique can be used to find the description of a job. The participant who works on the job is asked questions by the researcher and his perspectives and feelings about particular incidents to evaluate the position.
How do you use the critical incident technique?
Critical Incident Technique is used by finding experts, asking them the right questions about a particular incident, asking them questions about their feelings towards the Incident, and repeat the steps.
Bluein Christian Author
Content Writer with experience of 6+ years. Have experience writing content for different industries, such as travel, education, fashion, and more. A creative person by birth and by profession. She loves learning new concepts and creating useful content about them. She loves traveling and is always up for new challenges.
DETAILED INDUSTRY GUIDES
Software Development - Step by step guide for 2024 and beyond | OpenXcell
Learn everything about Software Development, its types, methodologies, process outsourcing with our complete guide to software development.
Mobile App Development - Step by step guide for 2024 and beyond | OpenXcell
Building your perfect app requires planning and effort. This guide is a compilation of best mobile app development resources across the web.
DevOps - A complete roadmap for software transformation | OpenXcell
What is DevOps? A combination of cultural philosophy, practices, and tools that integrate and automate between software development and the IT operations team.
MORE WRITE-UPS
17 Best AI Productivity Tools to Skyrocket Your Efficiency

Manushi Khambholja
In this day and age, we are surrounded by digital technologies, which are honestly making us less active in every aspect of life. So why don’t we turn the tables…

Top 45+ Generative AI Tools for Enterprises and Creatives
The world of AI is brimming with innovation, and generative AI is at the forefront. These powerful generative AI tools are like magic wands, capable of creating entirely new content…

Future-Oriented Generative AI Applications For Your Business!

Vaishnavi Baghel
“According to a McKinsey study, about 75% of generative AI applications fall under customer services, marketing, sales, and R&D. The same study also found that using Generative AI can increase…

Get a quote now!
- 15+ years of industry experience
- 1000+ global base of customers
- 500+ qualified resources
- ISO 9001:2008 certified
- CMMI level 3 company
- Transparent cost
- State-of-the-art facilities
- Quick product delivery
- Team ownership
Marketing91
Critical Incident Method and Technique – Definition, Process, Advantages
April 11, 2021 | By Hitesh Bhasin | Filed Under: Human Resources
The critical incident method, also known as the critical incident technique, is a process that uses a set of procedures to collect, observe, and analyze human behavior at specific events where an employee or an individual performs well and the circumstances where he could have performed better. It is a useful tool for performance appraisal
In the critical incident technique, the observer keeps a vigilant eye on the critical human behavior, incidents that occur, and the skills that an employee uses in the workplace. The manager provides a detailed critical incident report, which is later used to develop psychological principles and tackle practical problems.
Table of Contents
The five-stage process of critical incident method
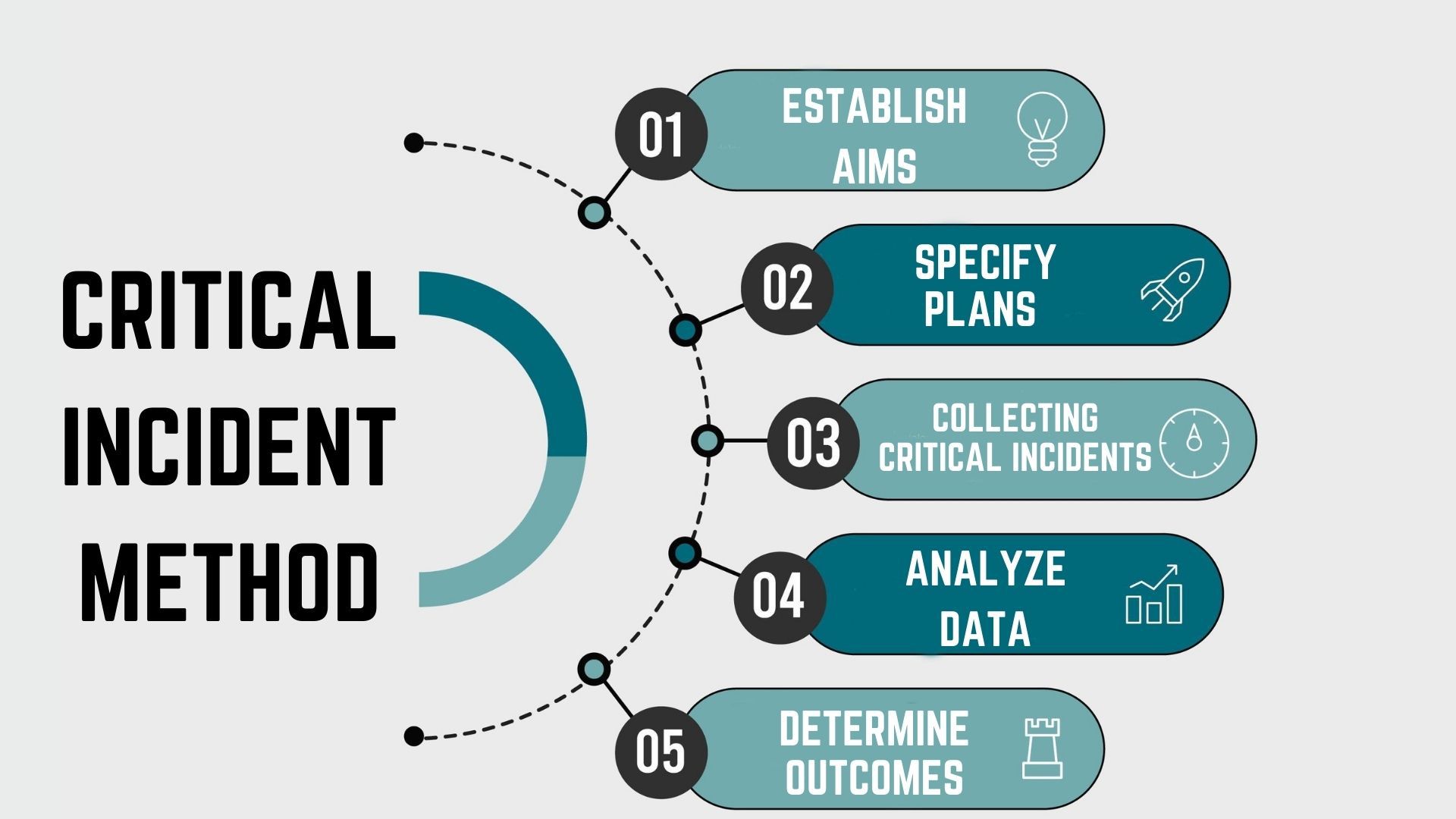
The critical incident technique is a five-stage process that has the following steps
1. Establish aims
The first stage establishes the aims of the activity. It lays down the groundwork that will determine what comes under the critical incident. This step involves identifying and reviewing the incidents that have occurred during the job.
An incident includes an account of what took place either through direct experience or observing the participant, for instance, a manager giving an account of what he saw. Some organizations like to help experts in defining the aim, especially those of activities that are not directly supervised by managers.
2. Specify plans and conditions
The second step of the five-stage critical incident technique is about laying down the conditions related to the general aims and plans for collecting incidents. The situations that have to be observed, who will be entrusted with the observation, and most importantly, who is being observed are all defined in clear terms.
An important step in this section is determining the best person for the job of providing incidents. He must be familiar with behaviors and conditions to make a useful critical incident report
3. Collecting critical incidents or facts
This step involves gathering information and finding facts about the incident’s incident during the job. Many researchers look at the critical incident interview to gather oral accounts but gathering written accounts is also essential.
This step also specifies the number of incidents that must be collected.
4. Analyze data
This step involves analyzing the information, facts, and data that has been collected from the participants by the researcher and determine any resulting issues. Categories of the behavior relevant to the study and how they will be subsequently used are determined.
This step is considered an inductive process that groups patterns and compares statements.
5. Determine outcomes and evaluate solutions
The researcher goes through the information, interprets, and then reports the findings. This step involves identifying the possible solutions for the problems that have already been identified.
The last step is evaluating whether the solution will eliminate the root cause of the problem that was identified.
The critical incident technique of performance appraisal
The steps taken for the critical incident method performance appraisal are as follows-
- A manager needs to start the discussion with an employee on an upbeat note. A friendly greeting sets the tone for the session and induces positivity in the environment.
- Layout the groundwork for the performance appraisal and tell the employees about the topics you will be covering and the order in which they will be addressed in this session. This will encourage an optimistic setting with a positive exchange that will lead to fruitful results.
- The next step in this process is to ask relevant questions. The answers will help in eliminating and resolving any existing issues
- It becomes crucial for the manager to maintain the focus on the activity on hand. The feedback should also be focused on the employee’s performance and not any other subjective or irrelevant things. Talk about developing competencies , handling critical incidents, achieving results, and meting objectives if you want to make the session a complete success
- Talk with the employees on a one-to-one basis and discuss the evaluations. Give them specific information to avoid misunderstandings. Provide the rationale behind the ratings you have given. You can also discuss the points and understand where both of you are agreeing and where you disagree
- Performance evaluation does not mean giving your opinion and having your say. Active listening is an integral part of the process where the superior tries to understand what the employee has to say. Rephrase and summarize to understand the employee properly
- This is an excellent opportunity to discuss and clarify the overall ratings with the employees. Give them information about the specific criteria that you have used to determine the results. This will help to clear most of the doubts from their mindset, and they will be assured that there has been no bias during the process
- The last and most important part of a critical incident performance appraisal technique is to end the session on a positive note. The manager should summarize the discussion, highlight the key points, ask the employees to sign the evaluations, and set follow-up dates for goal-setting
The advantages of the critical incident technique are as follows-
- Other methods put their onus on common events, whereas the critical incident report focuses on identifying rare events
- The critical incident analysis is considered advantageous as it provides important information
- It is a cost-effective method and is considered beneficial for an organization
- The perspective of the respondent is taken into account, and he is not forced to be a part of any framework related to the critical incident report
Disadvantages
The disadvantages of the critical incident technique are as follows-
- Several incidents are not reported for the simple reason that the observer might have forgotten them
- The reports might not be as precise as they should be
- The chance of bias is greater
- The incidents might not have taken place during the job and thus are meaningless
The critical incident method helps define the abilities, skills, knowledge, and competencies required for a task. It is especially helpful during job description and job specification as it aids in attracting the right talent for the job.
Liked this post? Check out the complete series on Human resources
Related posts:
- Staffing Process – 11 Importance Steps In Staffing Process
- Diversity Training – Definition, Meaning, Process and Objectives
- Talent Acquisition – Definition, Importance, Process and Tips
- What Is a Demotion? Definition, Meaning, Types and Process
- Performance Appraisal Process: Meaning, Types, and Objectives
- What is Recruitment Process Outsourcing (RPO) Concept?
- Peer Mediation | Purpose, Process, Types and Characteristics
- Acculturation – Overview, Process and Strategies
- Employee Relations | Definition, Meaning Importance and Advantages
- Employment at will – Definition, Meaning, Exceptions, Advantages
About Hitesh Bhasin
Hitesh Bhasin is the CEO of Marketing91 and has over a decade of experience in the marketing field. He is an accomplished author of thousands of insightful articles, including in-depth analyses of brands and companies. Holding an MBA in Marketing, Hitesh manages several offline ventures, where he applies all the concepts of Marketing that he writes about.
All Knowledge Banks (Hub Pages)
- Marketing Hub
- Management Hub
- Marketing Strategy
- Advertising Hub
- Branding Hub
- Market Research
- Small Business Marketing
- Sales and Selling
- Marketing Careers
- Internet Marketing
- Business Model of Brands
- Marketing Mix of Brands
- Brand Competitors
- Strategy of Brands
- SWOT of Brands
- Customer Management
- Top 10 Lists
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
- About Marketing91
- Marketing91 Team
- Privacy Policy
- Cookie Policy
- Terms of Use
- Editorial Policy
WE WRITE ON
- Digital Marketing
- Human Resources
- Operations Management
- Marketing News
- Marketing mix's
- Competitors
- DOI: 10.1177/1049732318813112
- Corpus ID: 58576760
The Critical Incident Technique: Method or Methodology?
R. F. Viergever
- Published in Qualitative Health Research 2 January 2019
- Medicine, Sociology
Figures and Tables from this paper

66 Citations
The critical incident technique (cit) in studying health care professional–patient communication.
- Highly Influenced
- 15 Excerpts
Critical incident technique helps determine how health library and information services influence clinical decision making and patient care: A literature review.
Safety on the ground: using critical incident technique to explore the factors influencing medical registrars’ provision of safe care, exploring social justice pedagogies in health and physical education through critical incident technique methodology, why medical residents do (and don’t) speak up about organizational barriers and opportunities to improve the quality of care, factors influencing non-conveyance care encounters in the ambulance service, registered nurses experiences - a qualitative study, the factors for success and lack of success in the breast cancer patient care pathway: a qualitative study from the health care staff perspective., health care workers’ experiences of workplace incidents that posed a risk of patient and worker injury: a critical incident technique analysis, why women die after reaching the hospital: a qualitative critical incident analysis of the ‘third delay’ in postconflict northern uganda, strategies for a safe interhospital transfer with an intubated patient or where readiness for intubation is needed: a critical incidents study., 83 references, the critical incident technique in service research.
- Highly Influential
- 10 Excerpts
The critical incident technique: a useful tool for conducting qualitative research.
The critical incident technique and nursing care quality research..
- 14 Excerpts
Critical incident technique as a qualitative research method.
Using the enhanced critical incident technique in counselling psychology research, inconsistent use of the critical incident technique in nursing research., developing flanagan's critical incident technique to elicit indicators of high and low quality nursing care from patients and their nurses., quality of the critical incident technique in practice: interrater reliability and users' acceptance under real conditions, the critical incident technique in dental research: a review, determinants of good and poor quality as perceived by us health care managers., related papers.
Showing 1 through 3 of 0 Related Papers

Published in Qualitative Health Research 2019
Log in using your username and password
- Search More Search for this keyword Advanced search
- Latest content
- For authors
- Browse by collection
- BMJ Journals
You are here
- Volume 14, Issue 9
- Experiences and actions of part-time firefighters’ family members: a critical incident study
- Article Text
- Article info
- Citation Tools
- Rapid Responses
- Article metrics
- http://orcid.org/0000-0002-2227-8754 Emelie Lantz 1 , 2 , 3 , 4 ,
- http://orcid.org/0000-0002-2990-3559 Bengt Nilsson 4 , 5 , 6 ,
- http://orcid.org/0000-0001-8376-8805 Carina Elmqvist 4 , 7 ,
- http://orcid.org/0000-0002-5412-9497 Bengt Fridlund 4 ,
- http://orcid.org/0000-0001-7479-8092 Anders Svensson 1 , 4
- 1 Department of Health and Caring Science , Linnaeus University , Växjö , Sweden
- 2 Research School for Doctoral Students within the Swedish Rescue Services, The Swedish Fire Research Foundation , Stockholm , Sweden
- 3 West Blekinge Fire and Rescue Service , Karlshamn , Sweden
- 4 Centre of Interprofessional Collaboration within Emergency care (CICE) , Linnaeus University , Växjö , Sweden
- 5 Department of Forestry and Wood Technology , Linnaeus University , Växjö , Sweden
- 6 Agunnaryd Voluntary Fire Brigade , Ljungby , Sweden
- 7 Department of Research and Development , Region Kronoberg , Vaxjo , Sweden
- Correspondence to Emelie Lantz; emelie.lantz{at}lnu.se
Objectives The purpose of this study was to describe the experiences and actions of part-time firefighters’ family members in rural areas in Sweden.
Design The study had an inductive descriptive design and used the critical incident technique.
Setting Rural areas, primarily served by a part-time fire station, across Sweden.
Participants The study included 25 participants (21 females and 4 males) with experiences of being a family member of a part-time firefighter. Family members who themselves served as firefighters were excluded.
Results Being a part-time firefighter’s family member was described into three main areas of experiences: ‘affecting everyday life’, ‘dealing with uncertainty’ and ‘being in this together’. Actions taken were divided into two main areas: ‘pursuing adaptations’ and ‘alleviating difficulties’.
Conclusions Family members of part-time firefighters faced increased responsibility at home, managing personal inconvenience and frustration. They offered emotional support for the firefighter, however, expressing a need for guidance on handling firefighters’ emotions and mental health after call-outs. Despite their crucial role, they often felt unrecognised by the fire and rescue service. Nonetheless, they took pride in their firefighter’s contribution to the community and noted positive impacts on the family.
- work satisfaction
- health services
Data availability statement
No data are available.
This is an open access article distributed in accordance with the Creative Commons Attribution Non Commercial (CC BY-NC 4.0) license, which permits others to distribute, remix, adapt, build upon this work non-commercially, and license their derivative works on different terms, provided the original work is properly cited, appropriate credit is given, any changes made indicated, and the use is non-commercial. See: http://creativecommons.org/licenses/by-nc/4.0/ .
https://doi.org/10.1136/bmjopen-2024-086170
Statistics from Altmetric.com
Request permissions.
If you wish to reuse any or all of this article please use the link below which will take you to the Copyright Clearance Center’s RightsLink service. You will be able to get a quick price and instant permission to reuse the content in many different ways.
STRENGTHS AND LIMITATIONS OF THIS STUDY
The inductive design employed in the study facilitated heightened comprehension of an under-researched area, contributing to the expansion of knowledge in the field.
The need for clearly defined critical incidents and accurate recollection by the participants is one limitation.
A potential limitation of employing the critical incident technique in this study is that it may have narrowed the scope to specific high-stress events.
Introduction
Balancing work as a non-career firefighter, for example, part-time or volunteer firefighter, with main employment and family obligations is challenging. This difficulty can lead to stress and dissatisfaction, which may ultimately result in firefighter resignations. 1–3 Even though these firefighters are the backbone of fire and rescue services (FRSs), especially in rural areas, recruiting and retaining them is a well-known challenge. 4–6 In Sweden, most firefighters are paid part-time firefighters (PTFs), usually serving on-call for 1 week per month. In contrast to other emergency personnel, PTFs are on-call from home, so the work-family interface is more pronounced. PTFs play an important role in public safety in rural areas; initiating an early response to emergencies, collaborating with the emergency medical services and by bringing valuable knowledge of the community they are part of. 7 8 However, PTFs struggle to find a balance between work as a firefighter and other commitments such as family time. 9 The family is an essential element in firefighter retention because they provide emotional support, help manage work-life balance and offer flexibility regarding the job’s demands. 9 This support helps firefighters cope with stress and manage their responsibilities, contributing to their overall well-being and job satisfaction, which in turn improves retention. There is a scarcity of research examining the interaction between family dynamics and high-risk occupations, 10 11 such as PTFs. However, a systematic review in this field, concludes that the mental health and well-being of spouses, partners and children of emergency responders is significantly affected by the demanding and stressful nature of emergency response work. Family members often experience heightened levels of stress, anxiety and mental health challenges due to the unpredictable and high-risk nature of their loved ones’ professions. 12
The literature examining the relationship between work and family has traditionally focused on the impacts on organisations and the individual employee. 13 14 Existing research has rarely focused on the effects that firefighters’ service has on family members. 15 16 Work and family cannot be viewed as separate spheres but rather as highly inter-related. The boundaries between these spheres are thus flexible, permitting factors such as stress to overflow from one sphere to another. There have been debates about whether work-related stress is transmitted from one family member to other family members. 17 18 The workplace culture, its demands and organisational support influence how firefighters’ family members perceive the efforts and rewards of the job in relation to the families’ needs and resources. 18 Family members’ mutual dependence and the availability of social support are factors that increase the family’s capabilities for managing challenges. 15 PTFs adjust their lives to fit with the service, which requires the support and commitment of the family. 9 Family members of PTFs play a vital supporting role, yet their experiences and actions remain poorly understood. This knowledge gap hinders policy development by FRSs in addressing firefighter retention. The purpose of this study was to describe experiences and actions of PTFs’ family members in rural areas in Sweden.
The study had an inductive descriptive design 19 and used the critical incident technique (CIT) developed by Flanagan. 20
Critical incident technique
The CIT was used to understand the experiences of, and actions taken by, family members of PTFs in critical situations related to the firefighters’ work situation. This method was created to describe experiences and actions in different contexts. 21 The CIT visualises both experiences and the subsequent actions taken in a well-defined, retrospective situation that affected a human activity, either positively or negatively. 21 Instead of reflecting attitudes or opinions, the goal of CIT is to characterise participants’ experiences and their actions taken during critical situations.
Settings and participants
Even if PTFs also serve in urban areas, they typically work in rural and sparsely populated regions, responding to emergencies in their local communities. In this study specifically, rural denotes an area primarily served by a part-time fire station, which means that the size and population of these areas vary. The inclusion criteria were being a family member of a PTF. The study strived to enrol participants with a variety of individual, family and work characteristics across Sweden, that is, a purposeful sampling, including a total of 25 participants ( table 1 ). Family members who were also serving PTFs were excluded. A family member was defined as a person denoted by the PTF as someone important for their work situation in their everyday life.
- View inline
Individual, family and work characteristics of part-time firefighters’ family members
Data collection procedure
FRS managers, with a geographical spread in Sweden, were informed about the study. In turn, they notified PTFs in their organisation, either all of them or a selected few, instructing them to contact someone in the research team. In some cases, the research team obtained the PTFs’ contact information directly. The firefighters acted as ‘gatekeepers’, deciding whether they wanted to ask their family member to participate. After obtaining contact information for the family members, one person in the research team made contact, explaining the study both orally and in writing. The participants did not receive any questions beforehand.
The interview guide was pilot tested with three participants, transcribed and discussed among the authors, to evaluate the guide. These interviews were then included in the study due to richness in content. The interviews were conducted via zoom or telephone by the first author. The study’s purpose was explained at the start of the interview. The participants were urged to provide descriptions of past situations that they considered had an impact and in which they took action, meaning situations that stood out from the ordinary. The interview guide contained a main question followed by nine questions about each critical incident according to Fridlund et al 21 ( table 2 ). Furthermore, probing and checking were used to provide well-developed, rich and detailed answers and to promote dialogue, such as “could you elaborate on that” or “explain what you mean by that”. All the interviews ended with a summary of the described situations being presented to the family members, with the participant being offered the opportunity to add more information or descriptions. The interviews lasted from 21 to 49 min. The interviews were audio recorded and the transcribed material was pseudo-anonymised before the data analysis process began within the research group. The audio file and text were stored on two separate encrypted servers (one for back up). The information letter included written information on handling personal data in compliance with the EU’s General Data Protection Regulation. The interviews were verbatim transcribed by the first author. Two participants dropped out before the scheduled interviews.
Description of the main question and the following nine interview questions in the critical incident technique according to Fridlund et al 21
Data analysis
The analysis was done manually by the authors. The first author began by reading the interview transcripts multiple times, extracting and condensing experiences and actions and assigning specific codes manually. 21 The aggregation of codes into subcategories, categories and main areas was also done through a manual, systematic sorting and individual analysis process. The mean number of critical incidents per participant were 4, generating 354 experiences and 151 actions. The experiences and actions were sorted and analysed separately, but the analysis process was the same for both. Codes relating to each other in terms of content were grouped together as subcategories at a descriptive level. Then similar subcategories were grouped together in categories. These categories were then grouped into main areas. The analysis of experiences included 32 subcategories, 7 categories and 3 main areas, while the equivalents for the corresponding actions were 13, 6 and 2, respectively. The authors conducted the analysis process together and discussed the results at every step of the analysis. The authors had thorough experiences of the CIT and was an interdisciplinary group. All authors were involved in the analysis process. It was a collaborative effort to scrutinising and systematising the data to validate the results at each step. All authors reached a consensus on the categories and areas that emerged, ensuring that the analysis was well-supported by the data. When a challenge or a diverse view arose, the authors revisited the transcribed interview to gain a comprehensive understanding and choose the most reasonable codes that best matched the data.

Patient and public involvement
Patients or public were not involved in the design of this study. However, all participants were informed in the information letter that the results should be disseminated in scientific journals, at conferences and as popular science publications. All participants were given the opportunity to sign up to receive the future published material.
Being a family member to a PTF was described according to experiences in three main areas: ‘affecting everyday life’, ‘dealing with uncertainty’ and ‘being in this together’ ( table 3 ). The actions taken were in two main areas: ‘pursuing adaptations’ and ‘alleviating difficulties’ ( table 4 ).
An overview of main areas, categories and subcategories (with number of experiences) regarding experiences of part-time firefighters’ family members
An overview of main areas, categories and subcategories (with number of actions) regarding actions taken by part-time firefighters’ family members
Experiences being a family member of a PTF
Affecting everyday life.
Being a family member of a PTF affected everyday life. It involved navigating daily demands and limitations during the on-call periods. This was particularly true when younger children were involved, as the firefighter could not care for them alone at home due to potential call-outs that required an immediate response. Consequently, the family member had to stay physically close to home or arrange backup support in case of call-outs, necessitating careful planning and adjustments:
Now it was my responsibility entirely, and he couldn’t do anything with the children.
This was experienced as an everyday problem that increased challenges and limitations, leading to the family member feeling restricted or being in a state of stand-by. However, there was an acceptance of this burden. It became a part of everyday life, even if it was inconvenient:
Life was like this all the time while having small children. It was a part of everyday life.
Balancing these aspects created a daily puzzle that demanded effort and imposed constraints on the family member, resulting in a sense of reduced ability to be spontaneous. Family members felt the need to align their lives with the on-call time. Although accepting it as a way of life, family members felt increased responsibility and required extra support to make it work.
Dealing with uncertainty
Family members of PTFs dealt with uncertainty due to call-outs. Firefighters encountered challenging situations and emotions during emergencies, and these difficult feelings extended into their home life, affecting family members. Coping with the mental health aspects of these experiences was challenging for family members, who often lacked the relevant knowledge or external support. However, being a support for the firefighter by engaging in open communication about their feelings became part of the family members’ experiences. Family members found themselves left alone whenever the firefighter was called out. These call-outs could occur at highly inconvenient times, leading to stress or frustration for family members. The family members had no information about how long the firefighter would be gone, ranging from minutes to a whole day. In an attempt to cope with the situation, family members wanted information about the call-out. Due to confidentiality, they were frequently left with uncertainty and gaps in knowledge:
I wanted to get a context, but he couldn’t provide it.
Night-time call-outs further impacted family members, disrupting their sleep:
I found it very uncomfortable when the alarm went off at night. I thought it was terribly unpleasant because then I had nothing to distract my thoughts, and they usually spun out of control.
Being in this together
Being a family member of a PTF involved being in it together. When someone took on the role of a PTF, it became a family decision that aimed to provide the necessary support during on-call periods so that everyday life still functioned. The increased workload on other family members led to negative emotions, such as frustration or disappointment:
But the emotions linked to it were, well, disappointment. That it didn’t turn out the way one had imagined.
It also involved stress and worry about the firefighter, both due to call-outs and long-term health consequences. Family members did not participate in the firefighter’s work context, leading to feelings of exclusion:
It was obvious, it wasn’t strange, but you felt left out. Because they had something together, and they’d experienced things together that no one else could come close to.
The on-call periods created friction in the relationship and everyday life, leading to a multifaceted experience of stress for the family members.
Nevertheless, it was a shared matter for the family, a joint decision. There was a financial aspect to the work, and a sense of give and take was involved. Firefighters often conveyed a genuine sense of joy in their work, which tended to positively influence the family. Family members described witnessing the firefighters’ joy and had a desire to make everyday life work so they could continue. Becoming and continuing to work as a PTF was often a mutual decision, highlighting the importance of communication and consensus within the family:
I thought it was a family thing to be part-time firefighters, you know. I thought it was, well, I mean a collective sacrifice.
The firefighters’ work situation also led to family members meeting new people, creating a new community context for firefighter families. Additionally, although family members felt negative emotions due to the firefighters’ work situation, it also brought positive effects and another perspective on life. PTFs that handled life-and-death situations brought home a new perspective on life and provided food for thought, influencing the family in a positive manner. Being a family member of a PTF was emotionally taxing, as family members navigated a delicate balance between their own inconveniences in everyday life and the community’s need for safety. However, family members expressed a sense of pride that also influenced their positive mindset.
Actions taken due to being a PTF’s family member
Pursuing adaptations.
Being a family member of a PTF entailed a pursuing way to adapt everyday life. These include taking increased responsibility for the home, children and the organisation of daily life. Due to the firefighter’s commitment to a specific proximity to the fire station, the family member became primarily responsible for tasks such as children’s dentist appointments, grocery shopping or walking the dog. This impacted both family time at home and their work commitments, requiring early departures for child pickups or facilitating transportation to activities. In addition to the role of the main caregiver for the children during on-call periods, the family member also took on the responsibility of addressing the children’s potential emotions, thoughts and disappointments when the firefighter had to respond to a call-out. During these situations, the family member had to handle matters independently, cultivating a problem-solving mindset even in the face of discouragement. Proactive planning before on-call periods became essential to effectively manage these heightened responsibilities. To be able to plan ahead when the firefighters left for a call-out, the family members sought information about the call-out and, if necessary, explored external support options:
One became quite skilled at planning and organising, you know, to make it work.
Family members set aside other commitments in favour of the firefighters on-call time, even adapting their work:
After all, his on-call service did lead to me changing my job as well.
Regardless of whether the family had children at home or not, the PTF’s family often did things separately due to the firefighter’s geographical limits around the fire station. Family members put their life and activities on hold during on-call periods.
Alleviating difficulties
Family members of PTFs alleviated the difficulties of family life. The family member was a significant support to the PTF, both in everyday life and emotionally. There was often a need for supportive communication after a challenging call-out:
So it was noticeable when you lived together. Something had happened, you know. And then you didn’t really know where the boundaries were, how much could you ask?
Family members did not have knowledge about what to do and where to turn if they noticed the firefighter having difficult emotions and mental health challenges after a call-out. They wanted to have a supportive conversation without impacting the confidentiality of the call-out. Family members also took action to assist during call-outs, providing food on the go or calling the main employer to inform them about the firefighter being away or late. Communication was vital to resolve friction in relationships due to the firefighter’s work situation. Even starting to work as a PTF was a joint decision, there were also ongoing conversations about whether he or she should continue as a firefighter due to the inconvenience.
The study findings shed light on the multifaceted role played by family members of PTFs by describing their experiences and actions. The findings reveal five main areas that offer valuable insight into this under-researched group, with both theoretical and practical implications.
Study findings
The findings highlight the complex interplay of responsibility, support and communication among family members of PTFs, which is discussed in the sections below.
The study findings underscore that being a PTF’s family member involves a significant increase in responsibility at home. The family member often becomes the primary caretaker for children and takes charge of daily tasks. The study reveals the need for proactive planning and organisation by family members to effectively manage the increased responsibilities of on-call periods. This corresponds with other literature that suggests that family members made sacrifices, and they shared strategies they use to mitigate the impact of their firefighter’s work. 22 One approach involved anticipating unexpected disruptions to their shared family and social time; a conscious decision to plan flexibly and actively preparing for unforeseen events and intentionally scheduling downtime when their firefighter was on-call. 22 The day-to-day pressures of emergency responder occupations significantly impact the health and well-being of spouses/partners and children, with spillover of work stress into family life, affecting mental health, well-being and family functioning. 12 Spouses often bear the burden of household responsibilities alone due to irregular work schedules. 23 However, this study also highlights the increased responsibility and the inconvenience that may be entailed in actioning this planning. Even if the family member is prepared for the firefighter leaving at any time, it nevertheless involves frustration or disappointment. To address some of this frustration and to alleviate the family member’s need for planning, a smart phone application with a time prognosis is valuable. Several Swedish FRSs use an application called Respons , designed to enhance communication and information management for emergency services. 24 Granting family members limited access to this tool could be beneficial, as it would aid in planning and reduce uncertainty through improved forecasting.
Family members emerge as a crucial source of emotional support for PTFs. The study reveals that after challenging call-outs there is a noticeable need for supportive communication. However, there is a recognition of the delicate balance between offering support and respecting the confidentiality of the call-out. These findings correspond with other literature in the work-family interface. Family-provided social support plays a crucial role in preserving the health and well-being of emergency responders. 12 While support may come from various sources, it appears that firefighters particularly value support from family and significant others, with support from co-workers and the organisation following closely behind. 25
Firefighters face significant psychological and physical challenges, and they must deal with irregular work schedules, time constraints and the need to perform in emergency situations regardless of the staff and resources that are available. 11 Furthermore, there were details about how emergency service workers experienced a sense of disengagement and emotional distance from their family members on returning from work. 26 Stress and symptoms experienced by the firefighter from a traumatic event can lead to a trauma response by family members; firefighter symptoms like mood swings and irritability are distressing enough to elicit a certain degree of traumatic reaction from their family members. 27 28 However, this study adds to the complexity of highlighting the need for information and knowledge for the family member in order to be able to address firefighters’ mental health and difficult emotions that arise from call-outs. The family is impacted by firefighters’ behaviour and moods, expressing the need for communication and alleviating emotions. Even though the literature highlights the importance of family members’ support for the firefighter’s well-being, 22 26 there is also a constant tension for the family members. They must balance their personal inconveniences in daily life with the community’s need for safety delivered by the PTFs. This creates a conflict between the safety of others and the individual’s own needs.
Family members experience inconveniences and increased responsibility at home, but it is hard to argue against the important work of PTFs in the community. This contrasts with families of full-time firefighters, who follow a regular schedule of being at work and then returning home during their off-time. PTFs, on the other hand, maintain regular work schedules and additionally have on-call responsibilities from home. Therefore, recognising and valuing the contributions of family members to PTFs are vital. Maintaining a healthy work-family balance is crucial for the long-term retention of firefighters, as it reduces the strain on their personal lives and encourages continued participation. 3 Furthermore, FRSs should strive to reduce the inconvenience for family members by offering support, recognition and practical initiatives, such as flexible schedules. By establishing support systems for family members, the FRS can help them to cope with the emotional challenges they face, for example, counselling services or resources for managing stress and anxiety.
This study describes how family members of PTFs see the joy their work brings which, in turn, has spill-over effects on the family. Family members also feel a sense of pride and contribution to the community. This corresponds with other literature that highlights how family members show strong support for and pride in the firefighters’ work. 18 Experiencing job satisfaction and a positive work environment also fosters a constructive atmosphere at home, resulting in the enjoyment of quality family time. 29 30 There is a mutual connection between family members and the FRS. 22 Family members employed terms like ‘our’, ‘we’ and ‘all of us’, when discussing the firefighters’ organisation, and exhibited a thorough understanding of factors such as community priorities, policies, operational procedures and specialised terminology. However, this does contrast with the findings were family members instead described feelings of being a bit set aside, or excluded or not appreciated by the FRS. They also felt that PTFs were strict about confidentiality, often excluding information when communicating with family members after a call-out. This draws parallels to a study on military spouses and families, who may also lack detailed information about the specifics of the employment due to security restrictions. This lack of information can significantly impact communication within the family unit. 31 The quality of communication in relationships involving emergency responders is significantly linked to their emotional responses and overall well-being. When both parties perceive a secure attachment, it leads to enhanced constructive communication and greater marital satisfaction. 23 To address these challenges, FRSs need to consider organising workshops or support groups that allows families to share their experiences and strategies, fostering new networks and relationships and helping them communicate about their feelings. Furthermore, another possibility is to implement more flexible on-call schedules to better accommodate the daily challenges faced by family members. In addition, the introduction of a carpooling system is a fitting help for families with their everyday activities.
Study methods
The study’s trustworthiness was achieved by addressing the concepts of credibility, dependability, confirmability and transferability throughout the research process. 32
To strengthen the credibility of the study, interviews were chosen as the method for data collection, as it allowed participants to express their thoughts in detail, facilitated by follow-up questions. Saturation was not addressed in the manner of Grounded theory. Instead, the number of critical incidents was determined by the study’s purpose, that is a purposeful sampling, rather than focusing on the quantity of participants, in accordance with Flanagan’s approach. 20 A potential limitation of employing the CIT in this study is that it may have narrowed the scope to specific high-stress events experienced by PFTs, potentially overlooking the broader impact of their work on daily life for both PTFs and their families. To strengthen the study’s dependability, participants from different parts of Sweden were intentionally chosen to represent a diverse range of age groups and years as a PTF’s family member. However, accurately and completely recollecting significant situations poses a challenge. There is a risk that the vividness and clarity of these memories may diminish over time, affecting the dependability of the data. The confirmability was reinforced by the authors performing the analysis together. The description of outcomes was discussed with all the authors to address biases and contemplate perspectives. The number of critical incidents gathered is determined by the scope of the study rather than the quantity of participants involved. 20 The findings are deemed potentially transferable to other contexts involving non-career firefighters, such as volunteer firefighters. Although non-career firefighters do not usually serve on-call, their families are still impacted by the uncertainty surrounding call-outs, which creates a parallel to the experiences of PTF families.
This study underscores the profound impact on the daily lives, emotional well-being and family dynamics of PTFs’ families. Family members balance their personal inconveniences with the community’s safety needs, navigating the conflict between their own needs and the demands of the firefighter’s role. Despite these challenges, they strive to provide emotional support and maintain open communication to address mental health aspects. The decision to become a PTF is a collective family commitment, fostering mutual support and shared responsibility.
Further research is needed regarding the work-life balance and identifying ways to improve it for PTFs and their families. Longitudinal studies will improve the understanding of the long-term effects of having a family member who works as a firefighter, including psychological well-being, equality, family dynamics and overall quality of life. Also, future research should further examine the effectiveness of support programmes designed specifically for the families of PTFs. This ought to include interventions to address the heightened responsibility at home, strategies for managing inconveniences and methods for enhancing support. Future research could benefit from incorporating a more comprehensive exploration of the holistic experiences of PFTs and their families, outside critical incidents, to provide a more nuanced understanding of the impacts of firefighting careers.
Ethics statements
Patient consent for publication.
Not applicable.
Ethics approval
The study was approved by the Swedish Ethical Review Authority (reg. no. 2023-02212-01). The study adhered to the principles outlined in the Declaration of Helsinki. 33 Oral and written information about the study were given to each participant before the interview. Participation was voluntary and the participants were informed that they could withdraw at any time and that all data would be treated confidentially. The participants provided written consent to their participation in the study.
- Cowlishaw S ,
- McLennan J , et al
- Burchielli R
- McLennan J ,
- Cowlishaw S , et al
- Almklov P ,
- Svensson A ,
- Elmqvist C ,
- Fridlund B , et al
- Nilsson B ,
- Elmqvist C , et al
- Johnson RC ,
- Eatough EM ,
- Chang C-H (Daisy) , et al
- Dyal M-A (Aimee) , et al
- Sharp M-L ,
- Solomon N ,
- Harrison V , et al
- Cramm H , et al
- O’Neill OA ,
- Rothbard NP
- Dimitropoulos G ,
- Bright E , et al
- Flanagan JC
- Fridlund B ,
- Henricson M ,
- Mårtensson J
- Lai C , et al
- Sommerfeld A ,
- Wagner SL ,
- Harder HG , et al
- Goldberg G ,
- Hertz MD , et al
- Repetti R ,
- Moreno-Jiménez B ,
- Sanz-Vergel AI , et al
- Ormeno MD ,
- Heller M , et al
- Lincoln Y ,
Contributors EL made substantial contributions to data collection, analysis and interpretation of data. She drafted the manuscript and gave final approval. She is the guarantor and responsible for the overall content of the manuscript. BN made substantial contributions to data analysis and interpretation of data. He reviewed the manuscript draft and gave final approval. CE made substantial contributions to the conception or design of the work and analysis. She reviewed the manuscript draft and gave final approval. BF made substantial contributions to the conception or design of the work and analysis. He reviewed the manuscript draft and gave final approval. AS made substantial contributions to data analysis and interpretation of data. He reviewed the manuscript draft and gave final approval.
Funding The study was funded by the Kamprad Family Foundation for Entrepreneurship, Research & Charity (reg. no. 20202001).
Competing interests None declared.
Patient and public involvement Patients and/or the public were not involved in the design, or conduct, or reporting, or dissemination plans of this research.
Provenance and peer review Not commissioned; externally peer reviewed.
Read the full text or download the PDF:
What is Incident Triage? Definition And Step-by-Step Process
The digital battlefield of cybersecurity is a constant struggle against ever-evolving threats. Here, the ultimate weapon is the ability to react swiftly and decisively to security incidents. Unchecked, these incidents can snowball, leaving a trail of destruction in their wake – crippled infrastructure, tarnished reputations, and a hemorrhaging bottom line. This is where the art of triage comes in, a crucial tactic borrowed from the fast-paced world of emergency medicine. Just as doctors prioritize critical patients, cybersecurity triage empowers teams to effectively sort and address incoming threats, ensuring the most critical vulnerabilities are addressed first.
This article explains why incident triage is so important, what its key steps are, and how AI changes the game of incident triage.
Why Incident Triage is Important
Imagine a busy emergency room. Nurses quickly assess incoming patients, prioritizing those in critical condition. This triage system is essential in saving lives. Similarly, incident triage is crucial in cybersecurity for organizations facing a constant stream of potential threats.
Incident triage acts as the first line of defense, establishing a structured approach to rapidly identify and respond to security incidents. A cyberattack can disrupt operations, lead to data breaches, and incur significant financial losses. By prioritizing critical incidents, triage helps organizations contain the situation quickly, reducing the overall cost of recovery.
Triage methods streamline operations by swiftly matching appropriate resources with specific tasks at the optimal moment. This guarantees that skilled professionals will promptly address critical incidents. Additionally, triage offers significant insights into the severity and urgency of each event, helping to avoid wasting time and resources on less critical issues. These insights also guide the development of future response strategies, enabling organizations to create more effective incident response plans and enhance their overall security measures.
Furthermore, incident triage builds trust both within an organization and with external stakeholders. Prompt and effective responses to security threats showcase a dedication to data security, fostering confidence among employees, customers, and partners in the protection of their data. Moreover, efficient triage procedures aid businesses in adhering to industry standards, regulations, and best practices. By emphasizing incident response, organizations show a proactive stance on protecting user data, ensuring ongoing compliance with continually changing regulations
Incident triage is not just a best practice – it’s a necessity in today’s cybersecurity landscape. It helps with optimizing resource allocation, and building trust with stakeholders – all vital aspects of maintaining a strong cybersecurity posture. Learn more about SOC alert triage .
The Complete Incident Triage Step-by-step Process
Effective incident response hinges on a well-oiled triage process. This 9-step approach equips security teams to swiftly analyze, prioritize, and tackle potential threats, efficiently safeguarding their organizations. Let’s take a look at these crucial steps and explore how to optimize them for maximum impact.
- Building a Streamlined Triage Process – First, clearly specify roles and responsibilities. Each team member should have a well-defined function within the triage process, ensuring no task falls through the cracks. Secondly, prioritize establishing effective communication channels. This allows for seamless information sharing and coordinated action throughout the triage process. Third, create a centralized system for tracking and managing all incoming alerts. This system fosters transparency and simplifies the process of prioritizing and resolving incidents. By meticulously constructing this well-defined triage process, you equip your team to handle alerts with swiftness and efficiency.
- Incident Reception and Assessment – Security teams tackle the initial detection and reporting of security events. This information can flood in from various sources like intrusion detection systems, firewall logs, or even employee reports. Once an incident lands on its plate, the security team springs into action, assessing its nature, scope, and potential impact. This initial evaluation is critical, as it lays the groundwork for the subsequent steps. By leveraging predefined data fields and event tags, the team can expedite classification and potentially automate the process, minimizing manual intervention and precious response time. Furthermore, implementing deduplication rules helps eliminate notification overload. This ensures responders focus their energy on unique incidents, not duplicates that can cloud judgment. Finally, the team leverages filters to distill essential details from the initial influx of information. Irrelevant data is cast aside, streamlining the triage process and boosting operational efficiency. The goal of this phase is to produce a well-classified incident report that offers a precise summary of the incident.
- Deduplication and Filtering – The dance of effective incident response relies on a delicate balance in managing incoming alerts. Implementing deduplication rules helps eliminate redundant alerts and notification overload, ensuring responders focus their energy on unique incidents. Filters are then applied to distill essential details from the initial influx of information, casting aside irrelevant data and streamlining the triage process. This optimization of alerting mechanisms strikes a crucial balance between timely notifications for actionable events and preventing alert fatigue. By prioritizing truly critical incidents, security teams can avoid being bogged down by constant alerts, allowing them to focus on the most impactful events. Ultimately, this approach fosters a more responsive incident management ecosystem, translating to a swifter resolution of security threats and minimal disruption to critical services.
- Prioritization in Incident Triage – This step ensures that valuable resources are allocated effectively, with the most pressing threats receiving immediate attention. Several factors influence an incident’s priority, including the severity of its potential impact, the value of the affected assets, and the likelihood of escalation. To optimize triage workflows and uphold service excellence, organizations should equip responders with clear prioritization guidelines. These guidelines can leverage automated mechanisms aligned with service and customer impact metrics. By expediting incident handling and resolution through automation, responders can focus their expertise on the most critical issues. Ultimately, effective prioritization ensures a well-oiled triage process, minimizing disruption and safeguarding the organization’s most valuable assets.
- Enrichment – This crucial step involves gathering and synthesizing additional context around the incident. Security teams leverage various data sources to paint a comprehensive picture of the threat landscape. By correlating information from threat intelligence feeds, asset management systems, and historical incident data, responders can uncover valuable insights that may not be immediately apparent. This enrichment process helps identify patterns, reveal potential attack vectors, and gauge the broader impact of the incident. Automated enrichment tools can significantly expedite this process, allowing for rapid data aggregation and analysis. The goal is to arm the incident response team with a wealth of relevant information, enabling them to make more informed decisions in the subsequent steps of the triage process. Ultimately, effective enrichment transforms raw data into actionable intelligence, setting the stage for a more targeted and efficient investigation.
- Investigation – With enriched data in hand, the security team delves into a basic yet crucial investigation to determine the authenticity and severity of the incident. This step involves a careful examination of the enriched data, system logs, and network traffic to identify any anomalies or indicators of compromise. Analysts may employ various tools and techniques, such as timeline analysis, log correlation, and malware sandboxing, to piece together the incident narrative. The investigation aims to answer key questions: Is this a genuine security incident or a false positive? What is the scope of the impact? Are there any ongoing malicious activities? By conducting this initial probe, the team can quickly distinguish between real threats and benign anomalies, ensuring that resources are allocated appropriately in the subsequent steps. This investigative process not only validates the incident but also lays the groundwork for more in-depth analysis if escalation becomes necessary.
- Escalation – Escalation becomes necessary for true positives requiring in-depth investigation. This involves forwarding the incident to a specialized team with the expertise to handle complex situations. For less critical incidents, immediate remediation takes center stage. The goal is to swiftly minimize the potential damage caused by the threat. By taking swift and appropriate action, organizations can effectively neutralize threats and minimize the potential impact on their systems and data.
- Communications – Transparent and active communication serves a dual purpose: managing stakeholder expectations and maintaining trust during an incident. By automating communication updates and providing stakeholders with real-time insights, organizations foster a sense of transparency and accountability. This proactive approach keeps stakeholders informed and reduces anxiety during potentially disruptive events. Furthermore, maintaining a public status page goes beyond simply informing stakeholders. It actively engages customers in the process, fostering a sense of partnership and shared responsibility. By providing a central hub for updates, organizations can effectively manage the flow of information, mitigate rumors, and ultimately strengthen their overall resilience to disruptions. In the end, effective communication becomes a cornerstone of successful incident triage, building trust and minimizing the negative impact of security threats.
- Learning from Every Triage – The triage process doesn’t end with resolving the immediate threat. Documentation plays a vital role in continuous improvement. Meticulously documenting your findings allows for a thorough review of the entire triage process. This review process allows you to identify areas for improvement, ensuring your team is constantly refining its approach to handling alerts. By learning from each triage experience, you can incrementally enhance your organization’s overall security posture. Ultimately, this focus on learning and adaptation ensures your triage process remains efficient and effective in the face of ever-evolving cyber threats.
By following this framework and leveraging the right tools, you can empower your team to efficiently identify potential threats and take decisive action to safeguard your organization.
What is AI-Enabled Incident Triage?
AI-enabled incident triage represents a relatively new approach to handling security incidents, leveraging the power of artificial intelligence (AI) and machine learning (ML) to empower SOC analysts. By analyzing vast amounts of data, identifying patterns, and learning from historical incidents, AI can significantly alleviate the burden on human analysts. This translates to more efficient SOC workflows. Traditionally, SOCs grapple with an avalanche of security alerts generated by various tools. The key to resolving this alert overload lies in expanding a SOC’s capacity to comprehensively review every alert. This is where AI enters the scene, offering a compelling solution. AI can go over all alerts and automatically analyze the content within each alert. This intelligent system can then dynamically select and conduct tests until it determines whether the alert signifies malicious activity.
The brilliance of this approach lies in AI’s ability to simultaneously review numerous alerts while conducting thorough investigations on each one. This surpasses the capabilities of human analysts by a significant margin. As a result, AI makes it possible to extract security value from various data types. By leveraging AI-enabled incident triage, SOCs can finally turn the tide against the ever-growing volume of alerts. This empowers them to identify and address threats with greater efficiency, ultimately strengthening their organization’s overall cybersecurity posture. Learn more about how AI-enabled incident triage works .
Extract the Value of Autonomous Triage Capabilities
In the ever-changing cyber threat environment, the traditional methods of incident triage are reaching a breaking point. The sheer volume and complexity of modern threats are rendering these legacy approaches unsustainable.
To stay ahead of this relentless tide, Security Operations Centers (SOCs) must embrace the future. AI-enabled autonomous incident triage solutions represent a transformative leap forward. These innovative solutions leverage the power of artificial intelligence to empower SOCs and revolutionize their approach to incident handling. What do we mean when we say autonomous incident triage? It’s quite simple actually. Automatically inspect all elements of suspicious alerts using an AI SOC analyst, then dynamically select and perform dozens to hundreds of tests to determine if an alert is malicious.
One of the most compelling benefits of AI-enabled triage is its dramatic impact on analyst workload. By automating a significant portion of the triage and investigation process, AI can reduce the burden on security analysts by up to 95%. Moreover, every single alert is meticulously triaged until a definitive verdict is reached – malicious or benign. This ensures that no potential threat slips through the cracks, safeguarding your organization from even the most obscure attacks. AI-powered triage injects a powerful dose of consistency into the incident triage process. Unlike human analysts who may be susceptible to fatigue or varying levels of experience, AI delivers unwavering consistency. Every incident, regardless of complexity, is meticulously triaged and investigated in a data-driven manner. The quality and efficiency of this analysis rival that of your most skilled security analysts.
Ready to get started?
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Development of a method and a smart system for tool critical life real-time monitoring.

1. Introduction
- Replace the tool when uniform flank wear on each edge exceeds 0.3 mm.
- Replace the tool when non-uniform flank wear on any edge exceeds 0.5 mm.
2. Research Methodology
2.1. signal analysis methodology, 2.1.1. spindle-load current sampling and analysis, 2.1.2. machining vibration sampling and analysis, 2.1.3. outlier detection using quartiles, 2.2. modeling method, 2.2.1. linear regression analysis, 2.2.2. multivariate linear regression, 2.3. experimental setup, 3. experimental design and data analysis, 3.1. the tool-life verification experiment, development of tool critical-life prediction models based on experimental data, 3.2. experiment on the correlation between tool wear and surface roughness, establish prediction rules for surface roughness during processing, 4. human–computer interface (hci) system, 5. experimental verification, 5.1. cutting experimental verification of tool critical life, 5.2. cutting experimental verification of surface roughness, 6. conclusions.
- In different materials, when the critical-life–current ratio exceeds the threshold value of 1.4 times, the flank wear is observed to be greater than the ISO-defined tool life wear of 0.3 mm. The results demonstrate that the current ratio threshold value has good universality in different materials, indicating that monitoring the machining current ratio to estimate the degree of tool wear is a feasible research direction.
- Based on a large number of experiments, the surface-roughness prediction rule established by this study was verified within the cutting parameter range of the preliminary experiment establishment. The average error between the experimental roughness measurement value and the predicted value was 10%. The average error in the verification outside the cutting parameter range of the preliminary experiment was 7.9%. The experimental results demonstrate that surface roughness can be predicted in real time by analyzing the changes in current characteristics.
Author Contributions
Data availability statement, acknowledgments, conflicts of interest.
- Fontaine, M.; Devillez, A.; Moufki, A.; Dudzinski, D. Modelling of cutting forces in ball-end milling with tool–surface inclination: Part II. Influence of cutting conditions, run-out, ploughing and inclination angle. J. Mater. Process. Technol. 2007 , 189 , 85–96. [ Google Scholar ] [ CrossRef ]
- Albertelli, P.; Goletti, M.; Torta, M.; Salehi, M.; Monno, M. Model-based broadband estimation of cutting forces and tool vibration in milling through in-process indirect multiple-sensors measurements. Int. J. Adv. Manuf. Technol. 2016 , 82 , 779–796. [ Google Scholar ] [ CrossRef ]
- Zhu, Z.; Guo, X.; Ekevad, M.; Cao, P.; Na, B.; Zhu, N. The effects of cutting parameters and tool geometry on cutting forces and tool wear in milling high-density fiberboard with ceramic cutting tools. Int. J. Adv. Manuf. Technol. 2017 , 91 , 4033–4041. [ Google Scholar ] [ CrossRef ]
- Altintas, Y. Prediction of cutting forces and tool breakage in milling from feed drive current measurements. J. Eng. Ind. 1992 , 114 , 386–392. [ Google Scholar ] [ CrossRef ]
- Soliman, E.; Ismail, F. Chatter detection by monitoring spindle drive current. Int. J. Adv. Manuf. Technol. 1997 , 13 , 27–34. [ Google Scholar ] [ CrossRef ]
- Li, X.; Djordjevich, A.; Venuvinod, P.K. Current-sensor-based feed cutting force intelligent estimation and tool wear condition monitoring. IEEE Trans. Ind. Electron. 2000 , 47 , 697–702. [ Google Scholar ] [ CrossRef ]
- Kim, T.Y.; Kim, J. Adaptive cutting force control for a machining center by using indirect cutting force measurements. Int. J. Mach. Tools Manuf. 1996 , 36 , 925–937. [ Google Scholar ] [ CrossRef ]
- Herwan, J.; Kano, S.; Oleg, R.; Sawada, H.; Watanabe, M. Comparing vibration sensor positions in CNC turning for a feasible application in smart manufacturing system. Int. J. Autom. Technol. 2018 , 12 , 282–289. [ Google Scholar ] [ CrossRef ]
- Tapia, E.; Lopez-Novoa, U.; Sastoque-Pinilla, L.; López-de-Lacalle, L.N. Implementation of a scalable platform for real-time monitoring of machine tools. Comput. Ind. 2024 , 155 , 104065. [ Google Scholar ] [ CrossRef ]
- Aldekoa, I.; del Olmo, A.; Sastoque-Pinilla, L.; Sendino-Mouliet, S.; Lopez-Novoa, U.; de Lacalle, L.N.L. Early detection of tool wear in electromechanical broaching machines by monitoring main stroke servomotors. Mech. Syst. Signal Process. 2023 , 204 , 110773. [ Google Scholar ] [ CrossRef ]
- Peta, K.; Stemp, W.J.; Chen, R.; Love, G.; Brown, C.A. Multiscale characterizations of topographic measurements on lithic materials and microwear using a GelSight Max: Investigating potential archaeological applications. J. Archaeol. Sci. Rep. 2024 , 57 , 104637. [ Google Scholar ] [ CrossRef ]
- Tapia, E.; Sastoque-Pinilla, L.; Lopez-Novoa, U.; Bediaga, I.; López de Lacalle, N. Assessing Industrial Communication Protocols to Bridge the Gap between Machine Tools and Software Monitoring. Sensors 2023 , 23 , 5694. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- ISO 8688-2:1989 ; Tool Life Testing in Milling—Part 2: End Milling. International Organization for Standardization, ISO: Geneva, Switzerland, 1989.
Click here to enlarge figure
| Name | Mode | Flutes | Helix Angle | Coating | Diameter (mm) |
|---|---|---|---|---|---|
| T1 | PPE0603 | 3 | 45° | TiSiN | 6 |
| T2 | PSE0604 | 4 | 35° | AlTiBin | 6 |
| Experiment Number | Cutting Width (mm) | Measured Wear (mm) | Measured Current Ratio | Predicted Current Ratio | Error (%) |
|---|---|---|---|---|---|
| 01 | 2 | 0.23 | 1.44 | 1.34 | 6.6 |
| 02 | 2 | 0.28 | 1.46 | 1.39 | 4.7 |
| 03 | 2 | 0.33 | 1.46 | 1.44 | 1.5 |
| 04 | 2 | 0.32 | 1.33 | 1.42 | 7.3 |
| 05 | 2 | 0.33 | 1.41 | 1.43 | 1.5 |
| 06 | 2 | 0.36 | 1.44 | 1.46 | 1.6 |
| 07 | 2 | 0.21 | 1.32 | 1.32 | 0.3 |
| 08 | 2 | 0.28 | 1.38 | 1.39 | 1.1 |
| 09 | 3 | 0.3 | 1.54 | 1.48 | 4.0 |
| 10 | 3 | 0.36 | 1.55 | 1.53 | 1.1 |
| 11 | 3 | 0.3 | 1.46 | 1.47 | 1.1 |
| 12 | 3 | 0.31 | 1.51 | 1.48 | 1.7 |
| 13 | 3 | 0.23 | 1.45 | 1.41 | 1.0 |
| 14 | 3 | 0.33 | 1.45 | 1.50 | 1.5 |
| 15 | 3 | 0.35 | 1.52 | 1.52 | 0.2 |
| 16 | 3 | 0.37 | 1.52 | 1.54 | 1.2 |
| 17 | 4 | 0.2 | 1.29 | 1.45 | 12.6 |
| 18 | 4 | 0.25 | 1.57 | 1.50 | 4.5 |
| 19 | 4 | 0.33 | 1.64 | 1.57 | 4.2 |
| 20 | 4 | 0.24 | 1.42 | 1.49 | 5.0 |
| 21 | 4 | 0.32 | 1.49 | 1.56 | 4.7 |
| 22 | 4 | 0.38 | 1.54 | 1.61 | 4.5 |
| 23 | 4 | 0.23 | 1.56 | 1.48 | 5.3 |
| 24 | 4 | 0.33 | 1.58 | 1.57 | 0.9 |
| 25 | 4 | 0.37 | 1.71 | 1.61 | 6.0 |
| Experiment Number | Cutting Width (mm) | Measured Wear (mm) | Measured Current Ratio | Predicted Current Ratio | Error (%) |
|---|---|---|---|---|---|
| 01 | 2 | 0.23 | 1.43 | 1.34 | 6.1 |
| 02 | 2 | 0.39 | 1.61 | 1.49 | 8.0 |
| 03 | 2 | 0.24 | 1.35 | 1.35 | 0.6 |
| 04 | 2 | 0.43 | 1.63 | 1.43 | 6.1 |
| 05 | 2 | 0.25 | 1.46 | 1.36 | 6.9 |
| 06 | 2 | 0.33 | 1.47 | 1.43 | 2.5 |
| 07 | 3 | 0.23 | 1.41 | 1.41 | 0.0 |
| 08 | 3 | 0.32 | 1.51 | 1.49 | 1.4 |
| 09 | 3 | 0.34 | 1.77 | 1.51 | 15.0 |
| 10 | 3 | 0.28 | 1.41 | 1.46 | 3.2 |
| 11 | 3 | 0.35 | 1.42 | 1.52 | 6.9 |
| 12 | 3 | 0.25 | 1.53 | 1.43 | 6.4 |
| 13 | 3 | 0.35 | 1.77 | 1.52 | 14.0 |
| 14 | 4 | 0.33 | 1.84 | 1.57 | 14.8 |
| 15 | 4 | 0.37 | 1.84 | 1.60 | 12.9 |
| 16 | 4 | 0.2 | 1.59 | 1.45 | 8.7 |
| Parameters | Value |
|---|---|
| Cutting width (mm) | 3 |
| Cutting depth (mm) | 0.5 |
| Feed per flute (mm/flute) | 0.005 |
| Hardness of material | HRC 55 ± 2 |
| Parameters | |
|---|---|
| Cutting width (mm) | 0.5 |
| Cutting depth (mm) | 0.5 |
| Feed per flute (mm/flute) | 0.02 |
| Hardness of material | HRC 20 |
| Surface Roughness (μm) | |||||||
|---|---|---|---|---|---|---|---|
| Measuring Point—Machining Cycle | First Machined Surface | P1-1 | P2-1 | P3-1 | P1-2 | P2-2 | P3-2 |
| First measurement | 1.28 | 1.39 | 1.22 | 1.22 | 1.24 | 1.46 | 2.60 |
| Second measurement | 1.29 | 1.44 | 1.21 | 1.28 | 1.32 | 1.36 | 2.58 |
| Third measurement | 1.26 | 1.47 | 1.27 | 1.23 | 1.30 | 1.35 | 2.45 |
| Fourth measurement | 1.26 | 1.50 | 1.27 | 1.27 | 1.25 | 1.30 | 2.41 |
| Fifth measurement | 1.24 | 1.48 | 1.21 | 1.21 | 1.30 | 1.41 | 2.46 |
| Average measurement value | 1.27 | 1.46 | 1.24 | 1.24 | 1.28 | 1.39 | 2.50 |
| Predictive value | 1.27 | 1.26 | 1.45 | 1.27 | 1.36 | 1.62 | 2.60 |
| Error (%) | 0.3 | 13.5 | 17.3 | 2.3 | 6.1 | 16.9 | 4.0 |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Wang, S.-M.; Tsou, W.-S.; Huang, J.-W.; Chen, S.-E.; Wu, C.-C. Development of a Method and a Smart System for Tool Critical Life Real-Time Monitoring. J. Manuf. Mater. Process. 2024 , 8 , 194. https://doi.org/10.3390/jmmp8050194
Wang S-M, Tsou W-S, Huang J-W, Chen S-E, Wu C-C. Development of a Method and a Smart System for Tool Critical Life Real-Time Monitoring. Journal of Manufacturing and Materials Processing . 2024; 8(5):194. https://doi.org/10.3390/jmmp8050194
Wang, Shih-Ming, Wan-Shing Tsou, Jian-Wei Huang, Shao-En Chen, and Chia-Che Wu. 2024. "Development of a Method and a Smart System for Tool Critical Life Real-Time Monitoring" Journal of Manufacturing and Materials Processing 8, no. 5: 194. https://doi.org/10.3390/jmmp8050194
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 05 September 2024
Larvicidal potential of Trachyspermum ammi essential oil and Delphinium speciosum extract against malaria, dengue, and filariasis mosquito vectors
- Alireza Sanei‑Dehkordi 1 ,
- Amir Masoud Tagizadeh 2 ,
- Mir Babak Bahadori 3 ,
- Elhameh Nikkhah 3 ,
- Masoumeh Pirmohammadi 4 ,
- Sara Rahimi 3 na1 &
- Hossein Nazemiyeh 5 na1
Scientific Reports volume 14 , Article number: 20677 ( 2024 ) Cite this article
Metrics details
- Drug discovery
- Medical research
- Microbiology
- Parasitic infection
- Pathogenesis
- Plant sciences
- Viral infection
Mosquito-borne diseases, such as malaria, dengue, and Zika, pose major public health challenges globally, affecting millions of people. The growing resistance of mosquito populations to synthetic insecticides underscores the critical need for effective and environmentally friendly larvicides. Although chemical pesticides can initially be effective, they often lead to negative environmental consequences and health hazards for non-target species, including humans. This study aimed to evaluate the larvicidal effects of Trachyspermum ammi essential oil and Delphinium speciosum extract on the larvae of three major mosquito species: Aedes aegypti , Anopheles stephensi , and Culex quinquefasciatus . Mosquito larvae of Ae. aegypti , An. stephensi , and Cx. quinquefasciatus were reared under controlled laboratory conditions. The larvicidal activity of T. ammi essential oil and D. speciosum extract was evaluated through standard bioassays, using various concentrations of essential oils (10, 20, 40, 80, and 160 ppm) and extracts (160, 320, 640, 1280, and 2560 ppm) to determine the lethal concentration (LC 50 ) values after 24 h of exposure. Fresh plant materials were collected, with the essential oil extracted via hydro-distillation, and the extract prepared using methanol solvent extraction. The chemical composition of T. ammi essential oil was examined using gas chromatography-mass spectrometry (GC-MS). Additionally, the preliminary analysis of the chemical compounds in D. speciosum extract was carried out using thin layer chromatography (TLC) and nuclear magnetic resonance spectroscopy (NMR) techniques. The results indicated that the essential oil of T. ammi exhibited more effective larvicidal activity compared to the D. speciosum extract. Specifically, the essential oil demonstrated LC 50 values of 18 ppm for Cx. quinquefasciatus and 19 ppm for Ae. aegypti . In contrast, the D. speciosum extract showed the strongest larvicidal effect against An. stephensi , with an LC 50 of 517 ppm. Concentrations of 40 ppm of the essential oil and 1280 ppm of the extract resulted in 100% mortality across all three species. Both the essential oil of T. ammi and the D. speciosum extract exhibited concentration-dependent larvicidal activity, and these results were statistically significant ( p < 0.001) compared to the no-treatment group. GC-MS analysis revealed thymol (88.95%), o-cymen-5-ol (4.11%), and γ-terpinene (2.10%) as the major constituents of the T. ammi essential oil. Additionally, TLC verified the presence of alkaloids in both chloroform and methanolic extracts. Proton NMR identified a diterpene structure for these alkaloids. These findings suggest that T. ammi essential oil is a promising candidate for natural mosquito control strategies. Given its efficacy, further research is warranted to explore its potential in integrated vector management programs.
Similar content being viewed by others
Larvicidal and adulticidal effects of some Egyptian oils against Culex pipiens

Ovicidal toxicity of plant essential oils and their major constituents against two mosquito vectors and their non-target aquatic predators
Evaluating larvicidal, ovicidal and growth inhibiting activity of five medicinal plant extracts on Culex pipiens (Diptera: Culicidae), the West Nile virus vector
Introduction.
Mosquitoes (Diptera: Culicidae ) are responsible for spreading important human parasites and microbes 1 , leading to major diseases and death, which impose a substantial economic burden globally 2 . Mosquitoes pose significant public health risks by transmitting diseases such as lymphatic filariasis, malaria, dengue fever, yellow fever, and Zika virus 3 . This emphasizes the crucial role of mosquito vector control in tropical and subtropical regions worldwide 4 , 5 , 6 .
Cx. quinquefasciatus plays a crucial role as a vector for both lymphatic filariasis and West Nile virus (WNV) 7 . Lymphatic filariasis, commonly referred to as elephantiasis, is recognized as one of the most significant neglected infectious diseases 8 and the second most common global mosquito-borne disease 9 . Over 882 million people in 44 countries worldwide remain threatened by lymphatic filariasis 10 .
Malaria is primarily transmitted to humans through the bites of infected female Anopheles stephensi 11 . In 2022, approximately 249 million cases of malaria were reported worldwide, resulting in 608000 malaria-related deaths across 85 countries 12 .
Dengue fever is a mosquito-borne viral infection that spreads to humans through the bites of infected mosquitoes, primarily Aedes aegypti mosquito 13 . Dengue has become a major global health issue, affecting approximately four billion people across 130 countries 14 . Annually, approximately 100–400 million infections occur, putting a significant portion of the world’s population at risk 14 .
While the treatment of these diseases is challenging, prevention offers a viable and effective strategy to reduce the burden of these disease and address the economic, emotional, and health consequences. Various approaches have been developed to manage vector populations and curb disease transmission in regions where these diseases are endemic 15 . Over the past several decades, synthetic insecticides have been employed to manage vectors and break the transmission cycle of vector-borne diseases 16 . However, the extensive use of synthetic pesticides to control mosquitoes presents significant risks, including toxicity to non-target organisms and potential harm to environmental and human health 17 , 18 . Additionally, the use of these synthetic chemicals contributes to the development of resistance in mosquito populations 19 .
Recent strategies to control mosquito vectors involve eco-friendly approaches, including the use of botanical insecticides. It is essential to explore environmentally friendly alternatives in botanicals, such as plant extracts and essential oils (EO) 20 . EOs are volatile compounds present in various plant families, including Asteraceae , Rutaceae , Myrtaceae , Lauraceae , Lamiaceae , Apiaceae , Piperaceae , Poaceae , Zingiberaceae , and Cupressaceae 21 . These natural insecticides are specifically toxic to mosquito pests while being environmentally beneficial. It is well-known that plant metabolites are toxic to mosquitoes and can effectively manage their populations 22 .
Botanical components possess antifungal, antibacterial, antileishmanial, antimalarial, and insecticidal properties 23 , 24 , 25 , 26 . Natural substances, such as EO and plant extracts, exhibit a wide range of biological effects, including insecticidal, acaricidal, repellent, antifeedant, ovipositional deterrent, and growth inhibiting properties against insect pests, including mosquitos 27 , 28 , 29 , 30 . EOs represent a substantial source of biologically active monoterpenes and have been extensively documented for their bioactivities against insect pests. Several EOs and extracts with notable potential for mosquito control originate from the plant genera Tagetes spp. 31 , Mentha spp. 32 , Citrus spp. 33 , Trachyspermum spp. 34 , and Delphinium spp. 35 . The larvicidal potency of extract from Thymus plant 36 , Satureja species 37 , Pelargonium roseum 38 , Carum copticum 39 , Citrus aurantifolia 40 against Cx. quinquefasciatus, An. stephensi, Ae, aegypti have been reported. Also, EOs derived from cassia, camphor, wintergreen, pine, and eucalyptus are already being utilized in various commercial products intended for mosquito control 41 .
Trachyspermum ammi is taxonomically classified under the Apiaceae family, which comprises approximately 347 genera and 12,816 species. The plant is widely distributed and cultivated in various regions, including Iran, Pakistan, Afghanistan, and India. The grayish-brown seeds (fruits) of T. ammi are commonly used for biomedical and nutritional proposes. The EO extracted from the seeds is a volatile oil possessing distinctive organoleptic and physicochemical characteristics 42 , 43 .
The Delphinium genus (Ranunculaceae) encompasses around 300 species globally, with 28 species found in Iran, including 9 species endemics to the region 44 . D. speciosum , a perennial herb found in Northwestern region of Iran, features villous stems that can grow up to 80 cm in height. These stems may be either simple or branched and are supported by woody roots. The leaves of this plant are rounded-pentagonal in shape, measuring between 3–12 mm in width, and are covered with villous hairs on both surfaces 44 . For many years, plants from the Delphinium genus have been traditionally used as herbal remedies, including insecticides, larvicides, antibacterial, and lice treatment 35 , 45 , 46 , 47 .
Despite the limited knowledge of the larvicidal properties of T. ammi and D. speciosum endemic to Iran, our study represents the first investigation into their effects against C. quinquefasciatus , An. stephensi , and Ae. aegypti . We also examined their chemical profiles, which could potentially be utilized for future biopesticide development.
Materials & methods
Mosquitoes rearing.
The mosquito larvae employed in larvicidal tests including Ae. aegypti , An. stephensi , and Cx. quinquefasciatus, were sourced from a laboratory colony at the Department of Biology and Control of Disease Vectors, Faculty of Health, Hormozgan University of Medical Sciences in Bandar Abbas, Iran. These colonies were consistently maintained at 27 ± 1 °C, with a 12:12 light and dark photoperiod, and 65 ± 5% relative humidity. The larvae were fed daily with powdered fish food until pupation, ensuring a continuous supply for mosquito larvicidal experiments.
Collection of plants material
The D. speciosum plant which was collected in May 2023 from the Sahand Mountain in the Sprakhon region of East Azarbaijan Province (37 °82′N, 46 °40′E; altitude of 2480 m), and a voucher specimen (TBZMED 5004) was deposited in the Herbarium of the Faculty of Pharmacy, Tabriz University of Medical Sciences. The T. ammi seeds were procured from Shafa Pajohan Sabz, a knowledge-based firm located in Tabriz, Iran. The collected plants were identified by Dr. Atefeh Ebrahimi, a botanist at the Herbarium of the Faculty of Pharmacy, Tabriz University of Medical Sciences. Harvesting of the plants was conducted in accordance with the regulations issued by the Natural Resources & Watershed Management Organization-I.R. of Iran and the Research Institute of Forests and Rangelands. According to these regulations, the harvesting of Delphinium plants for laboratory purposes is permitted without restrictions.
Plant extract preparation
Following the collection and washing of D. speciosum , the plant was subjected to a drying process under laboratory conditions. The aerial parts of the plant were then pulverized and subjected to extraction via the Soxhlet method, utilizing petroleum ether, chloroform, and methanol sequentially. A portion of the resulting crude methanolic extract, weighing 5 g, was subsequently employed for bioassay analysis. Different concentrations (160, 320, 640, 1280, and 2560 ppm) were derived from the stock solution 48 , 49 .
Essential oil extraction
The T. ammi seeds were pulverized, and their essential oil was extracted using hydro-distillation with a Clevenger apparatus over a period of 3 h. The essential oil was subsequently dried using anhydrous sodium sulphate and preserved at a temperature of −4 °C for use in larvicidal bioassay tests 50 .
Larvicidal bioassay
Bioassay tests were conducted in accordance with the World Health Organization’s standard method 51 . Total T. ammi essential oil and D. speciosum extract were initially dissolved in 99% ethanol and 99% methanol, respectively, as co-solvents. The solutions were stirred for 30 s with a glass rod. For the larval test, 25 larvae at the late 3rd and early 4th instars of Ae. aegypti , An. stephensi , and Cx. quinquefasciatus were collected using a fine mesh strainer and then gently transferred by tapping into four 400-mL glass beakers containing 249 mL of dechlorinated tap water. Each concentration was replicated at least four times, comprising a total of 100 larvae. The test medium was prepared by combining 1 mL of the appropriate dilution of essential oil or total extract in co-solvents with 249 mL of water. Controls included batches of mosquitoes from the colony exposed to water and the solvents alone. The larvae were exposed to different concentrations of 10, 20, 40, 80, and 160 ppm of essential oil, and 160, 320, 640, 1280, and 2560 ppm of total extract in dechlorinated tap water for 24 h, with no provision of food during this period.
Gas chromatography/Mass spectroscopy analysis
The composition of T. ammi EO was analyzed using a chromatography-mass spectrometry instrument (Shimadzu, QP-5050 A) equipped with a DB-1 capillary column (60 m length, 0.25 mm inner diameter, and 0.25 μm film thickness). An electron impact ionization (EI) system applying 70 eV ionization energy was used for the identification of the essential oil’s volatile components. Helium was employed as the carrier gas at a flow rate of 1 mL/min, operating in constant linear velocity mode. The injector and detector temperatures were set at 250 °C. The oven temperature was held at 50 °C for 3 min and then was programed from 50 to 265 °C at the rate of 2.5 °C/min, and was kept at this temperature for 6 min. After dilution of the essential oil in n-hexane (1:100), 1 µL of essential oil solution was injected manually.
Identification of each volatile component was carried out using calculated retention indices (RI) based on n-alkanes chromatogram (C 8 –C 24 ) under the same gas chromatography condition. The EO constituents were identified by comparing their RI values and mass spectra with those in several Mass Spectral libraries such as Wiley and NIST. The results are presented as the area of Mass response in relative percentages 52 .
NMR analysis of extracts
Since Delphinium species are mainly known for having diterpene alkaloids, and most published sources consider these compounds responsible for the anti-parasitic effects of these plants, so it was tried to check the presence or absence of alkaloid compounds in the used extracts. A preliminary study was conducted to determine the alkaloid content of the extracts using TLC on precoated-silica gel plate (TLC Silica gel 60 F254, Merck). Additionally, NMR spectroscopy was used to determine the nature of alkaloids in the extracts. It should be noted that the NMR guided isolation method is a valuable technique that has been widely used by researchers in metabolomic studies and drug discovery. This very powerful tool provides the ability to detect different categories of chemical compounds in the extract at the same time 53 , 54 , 55 , 56 , 57 . NMR experiments were recorded with a Bruker UltraShield-400 spectrometer (Bruker, Germany) in deuterated chloroform and TMS used as an internal standard.
Statistical analysis
In the current study, the independent variables include different larval species and treatment groups exposed to various concentrations of essential oils and plant extracts, while the dependent variable is the mosquito mortality rate. All experiments were conducted in quadruplicate, data are expressed as mean ± standard deviation. We assessed the normality of the dependent variable using graphical methods and statistical tests. Due to the large sample size, the central limit theorem supports the assumption of normality in the data 58 . Lethal concentrations (LC 50 and LC 90 ), along with 95% confidence intervals and probit equations, were determined through probit regression analysis. A Three-Way ANOVA followed by Tukey’s HSD test (95% confidence interval, SPSS v.25) was used to compare larvicidal activity. Graphs were generated using GraphPad Prism v.8. Statistical significance was defined as p < 0.05. The effect size (ES) was calculated using Cohen's d, which is defined as the difference between two means divided by the pooled standard deviation. Cohen's guidelines for interpreting effect size are: small effect: d ≈0.2, Medium effect: d ≈0.5, Large effect: d ≈0.8. This quantification provided an objective measure of the practical significance of the findings 59 .
Larvicidal effect of samples
In this study, we examined the larvicidal effect of T. ammi essential oil at different concentrations ranging from 10 to 160 ppm and D. speciosum extract at various concentrations between 160 and 2560 ppm on three mosquito species: An. stephensi , Cx. quinquefasciatus and Ae. aegypti . The findings are summarized in (Table 1 ).
As shown in Table 1 , The An. stephensi demonstrated the highest larval mortality rate when treated with D. speciosum extract, reaching 100% mortality at a concentration of 1280 ppm. For Cx. quinquefasciatus and Ae. aegypti larvae treated with this extract, mortality rates at the highest concentration of 2560 ppm were 98 and 99%, respectively. The lowest mortality rate was observed in Cx. quinquefasciatus larvae treated with D. speciosum extract, showing only 5% mortality at a concentration of 160 ppm. For larvae treated with T. ammi EO, the highest mortality rates were observed in Cx. quinquefasciatus and Ae. aegypti , with mortality rates of 96% and 94%, respectively, at a concentration of 40 ppm. In contrast, the mortality rate for An. stephensi larvae treated with 40 ppm of T. ammi EO was reported to be 45%. The lowest larval mortality rates at 10 ppm of T. ammi EO were recorded as 6% for An. stephensi , 13% for Cx. quinquefasciatus , and 11% for Ae. aegypti .
A clear dose-dependent relationship was observed between the concentration of T. ammi EO and D. speciosum extract and the mortality rates of mosquito larvae. As the concentration of T. ammi EO increased, the mortality rates among An. stephensi , Cx. quinquefasciatus , and Ae. aegypti also increased significantly. Specifically, at lower concentrations (10 and 20 ppm), mortality rates ranged from 13 to 54%, while at higher concentrations (160 ppm), mortality rates reached up to 99% for An. stephensi and 100% for Cx. quinquefasciatus and Ae. aegypti . Similarly, D. speciosum extract exhibited a dose-dependent effect, with mortality rates increasing from 10, 5, and 6% at 160 ppm to 100% at 2560 ppm for An. stephensi , Cx. quinquefasciatus , and Ae. aegypti . Statistical analysis confirmed a significant dose-dependent relationship ( p < 0.05) between the concentration of T. ammi EO and D. speciosum extract and larval mortality, indicating that both are effective larvicides, with higher concentrations leading to increased mortality in mosquito populations (Table 2 ).
The results of this study also revealed that the average mortality rates differed significantly among the various larval species ( p < 0.02). The ANOVA test indicated statistically significant differences in average mortality rates between An. stephensi and Cx. quinquefasciatus ( p = 0.03), as well as between An. stephensi and Ae. aegypt ( p = 0.04). However, the difference in average mortality rates between Cx. quinquefasciatus and Ae. aegypti was not statistically significant ( p = 0.06( (Table 3 ).
A significant difference in the average larval mortality percentage was observed among the treatment groups ( p = 0.001). The post-hoc ANOVA tests revealed a significant difference between the groups treated with T. ammi EO and D. speciosum extract ( p = 0.02). Additionally, the average mortality percentage in the groups treated with either T. ammi EO or D. speciosum extract was significantly higher compared to the untreated group ( p < 0.001) (Table 3 ).
The average mortality percentage varied across groups with different therapeutic concentrations, and this variation was statistically significant ( p = 0.001). In the T. ammi EO treatment group, concentrations ranging from 20 to 160 ppm showed a significant difference compared to the untreated group ( p < 0.001), while the 10 ppm concentration did not exhibit a statistically significant difference ( p = 1.00).
In the group treated with D. speciosum extract, concentrations between 640 and 2560 ppm exhibited a significant difference compared to the untreated group ( p < 0.001), while the 10 ppm concentration did not show a significant difference from the untreated group ( p = 0.98) (Table 3 ).
The comparison of larval mortality percentages at different concentrations in the two treatment groups, T. ammi and D. speciosum , indicated no statistically significant difference between the highest concentration of D. speciosum (2560 ppm) and the concentrations of 40, 80, and 160 ppm of T. ammi ( p > 0.05). Additionally, the lowest concentration of T. ammi (10 ppm) did not show a statistically significant difference compared to the concentrations of 160 to 640 ppm of D. speciosum ( p > 0.05). However, the mortality percentages at other concentrations in the two treatment groups differred significantly ( p < 0.05).
The mean difference (MD) and standardized mean difference (SMD) values, as well as the interpretation areas of the effect size, have been calculated and presented in (Tables 4 , 5 ). The effect size interpretation showed that concentrations of 1280 and 2560 ppm of D. speciosum were more effective in increasing larval mortality rate compared to other concentrations tested (Table 4 ). Additionally, the concentrations of 40, 80 and 160 ppm of T. ammi were identified as highly effective (Table 5 ).
According to the dose-response curve shown in (Fig. 1 ), the LC 50 value for the essential oil derived from T. ammi was calculated as 48.7, 18.3, and 19.7 ppm for An. stephensi , Cx. quinquefasciatus and Ae. aegypti , respectively. The LC 50 value for the extract of D. speciosum was determined as 517, 991.5, and 887.4 ppm for An. stephensi , Cx. quinquefasciatus and Ae. aegypti , respectively.

Dose-response curves depicting the larvicidal activity. ( a ) extract of D. speciosum ( b ) EOs of T. ammi .
Probit regression analysis of larvicidal data, shown in (Table 6 ), determined the LC 50 and LC 90 values for D. speciosum ’s extract and EO of T. ammi . The LC 90 value for the EO was calculated as 143.3, 35.8, and 40.2 ppm for An. stephensi , Cx. quinquefasciatus and Ae. aegypti , respectively. The LC 90 value for the extract was determined as 1157, 2662, and 2530 ppm for An. stephensi , Cx. quinquefasciatus and Ae. aegypti , respectively.
Essential oil composition
Chemical compounds of the EO of T. ammi are presented in (Table 7 ). The volatile oil was characterized by the presence of 6 constituents, representing 98.09% of the total compounds. Thymol (88.95%), o-cymen-5-ol (4.11%), and γ‑terpinene (2.10%) were identified as the most abundant phytochemicals. All of the compounds belong to monoterpenes. Oxygenated monoterpenes are the main class of compounds in EO composition. The remaining compounds belong to hydrocarbon monoterpenes (Table 7 ).
Extract composition
TLC method was used to confirm the presence of alkaloids. Spraying the dragendroff reagent on the TLC surface revealed the orange spots of alkaloids (Fig. 2 ). The resulting chromatogram showed that alkaloids are present only in the chloroform and methanolic extracts, and the petroleum ether extract does not contain these compounds. Examination of proton NMR spectra showed that the alkaloids in the chloroform and methanol extracts have a diterpene structure (Fig. 3 ).

TLC profile of alkaloids in different extract of Delphinium speciosum aerial part: 1- MeOH, 2-Chloroform extracts on Silica gel GF254 using Hexane: Chloroform: Methanol (11.5; 5: 0.5) as developing solvent mixtures. A dragendorff spsray reagent was used for detection of alkaloids.

NMR chromatogram of alkaloids in different extract of Delphinium speciosum aerial part ( a ) chloroformic ectract; ( b ) methanolic extract. The 1H-NMR spectra were recorded in CDCl3 in 400 MHz.
The development of eco-friendly and safe insecticides derived from natural sources, such as plants, is vital due to their precise targeting abilities and reduced risk of bioaccumulation. Utilizing natural control methods, like biopesticides, offers an effective strategy to combat insecticide resistance in mosquitoes 60 , 61 . In this study, we evaluated the efficacy of T. ammi essential oil and D. speciosum extract as larvicides against mosquito vectors of malaria, dengue fever, and filariasis.
Our study demonstrated the strong larvicidal effects of D. speciosum extract and T. ammi EO against three primary mosquito vectors: An. stephensi , Cx quinquefasciatus , and Ae. aegypti . These results are consistent with previous studies that investigated the toxic activity of Delphinium cardiopetalum extract against agricultural pest larvae 62 . Similar studies have demonstrated that extracts from Delphinium cultorum exhibit strong larvicidal effects on Ae. aegypti larvae 63 . The current study found mortality ratees ranging from 6 to 99% in Ae. aegypti , 10 to 100% in An. stephensi , and 5 to 98% in Cx. quinquefasciatus larvae treated with D. speciosum extracts at concentrations of 160 to 2560 ppm. These findings align with the 30–90% mortality observed in studies that reported significant larvicidal activity of 31 Delphinium species extracts against mosquito larvae 64 . Also, the findings of this study are consistent with previous research that reported significant larvicidal effects of Delphinium staphisagria against Leishmania spp, with a 100% mortality rate at 400 ppm 65 , which is higher than the 30–87% mortality rate at 200–1600 ppm observed in Ae. aegypti 35 , 66 .
In contrast to previous studies that indicated minimal insecticidal activity of Delphinium staphisagria against Pediculus species 67 , our study revealed a strong efficacy of D. speciosum extract against Ae. Aegypti, achieving a mortality rate of 99% at 2000 ppm. Our findings are also consistent with studies showing that the green synthesis of silver nanoparticles using Delphinium denudatum root extract possesses both antibacterial and mosquito larvicidal properties, with reported mortality rates of 95% at 4000 ppm in mosquito larvae 47 .
Many other studies have also shown that extracts from different plants have strong larvicidal effects on An. stephensi and Cx. quinquefasciatus , with reported mortality percentages ranging from 5 to 90%, which closely align with the results of our study 20 , 68 , 69 , 70 , 71 , 72 .
The results of previous studies showed that the EO of T. ammi seeds has moderate larvicidal effects on small hive beetles ( Aethina tumida), with a mortality rate of 36.25% at the highest concentration (48 ppm). In contrast, the results of our study shows that the mortality rate of the important vector species at a concentration of 40 ppm was 96% 73 . T. ammi exhibited high potency against larvae in this study, with a similar effect recorded against Cx. quinquefasciatus , Ae. aegypti , and An. stephensi, achieving mortality rates of 90, 97, 100%, respectively 41 , 43 , 74 . While only a few studies have explored the larvicidal effects of D. speciosum extract and T. ammi EO, many studies have focused on the larvicidal properties of EOs from other plants on important vector species. A similar finding has been recorded for Cx. quinquefasciatus , Ae. aegypti , and An. stephensi 20 , 71 , 75 ,
Consistent with our results, several past studies have reported statistically significant variations in the susceptibility of different mosquito larvae to plant-derived larvicides 33 , 76 , 77 , 78 . However, in contrast to our findings, a few previous research have reported no statistically significant differences in the larvicidal efficacy of plant extracts across different mosquito species 79 , 80 .
The statistically significant differences in the average larval mortality can be attributed to several factors. First, there is a variation in larval physiology and biochemistry, meaning different larval species may have different physiological and biochemical responses to the same treatment. Second, there is a differential penetration or mode of action of the larvicides, which means that the effectiveness of the larvicides can vary depending on how they penetrate the larvae or their mode of action 81 , 82 . These statistically significant differences in the average larval mortality underscore the importance of considering species-specific responses when developing and deploying plant-derived larvicides.
The results of our study indicated that T. ammi EO demonstrated stronger larvicidal activity than D. speciosum extract against all tested species. This increased effectiveness is attributed to its higher concentration of bioactive compounds. These EOs disrupt larval physiological processes and possess antimicrobial properties, which may enhance their effectiveness 72 . This finding aligns with previous studies, further confirming the superior efficacy of essential oil 83 , 84 . EO with an LC 50 value less than 50 ppm are deemed very active, those between 50 and 100 ppm as active, and those over 100 ppm are considered weak or inactive 85 . For extracts, toxicity varies with LC 50 values: under 100 ppm is highly toxic, 100–500 ppm is moderately toxic, 500–1000 ppm is low toxicity, and above 1000 ppm is non-toxic 86 . Based on this classification, the LC 50 of T. ammi EO and D. speciosum extract from our study categorizes them as highly toxic and moderately toxic against all three vector species, respectively.
Our findings revealed that both plant-derived larvicides exhibited significant, dose-dependent larvicidal activities across all tested mosquito species, which are in line with the results of previous studies 33 , 72 , 78 , 83 . The LC 50 of the T. ammi EO against An. stephensi larvae was 49 ppm, which is lower than the LC 50 (81 ppm) reported for the same EOs in a previous study 41 . Similarly, the LC 50 values of the EO from T. ammi against Ceratitis capitata , Tribolium castaneum , and Aethina tumidawas were reported to be 46, 15, and 52 ppm, respectively 34 , 73 , 87 , and the LC 50 of the D. speciosum extract against Aedes larvae was 887 ppm, which is notably higher than the LC 50 (244 ppm) documented for the same crude extract in another investigation 35 .
The effect size analysis of this study revealed that D. speciosum extract exhibited potent effects solely at concentrations of 1280 and 2560 ppm. In contrast, T . ammi essential oil demonstrated effects ranging from moderate to strong at concentrations between 20 and 160 ppm. Moreover, based on our knowledge, there were no reports found on the effect size of the larvicidal impact of D. speciosum extract and T. ammi EO against An. stephensi , Cx. quinquefasciatus , and Ae. aegypti . The findings on effect size and effective concentration were highly beneficial for enhancing larval mortality rates and applying them in real-world scenarios. In this research, the practical concentrations used were 1280 ppm for D. speciosum and 40 ppm for T. ammi .
Previous studies reported that γ‑terpinene, carvacrol, p-cymene, and thymol were the main phytochemicals in the EO of T. ammi 52 , 88 , 89 , 90 , 91 , 92 , 93 , 94 , 95 . These studies investigated different chemotypes of T. ammi from different localities using various extraction methods. Our findings on the chemical constituents of the plant are consistent with previous findings. The minor differences in the chemical compositions reported by different studies may be associated with variable climate, geographical conditions, genetics, and extraction techniques. Previous studies show that most of the alkaloids in the genus Delphinium have diterpene structures 96 . As shown in our results, several alkaloid compounds were observed in chloroform and methanolic extracts.
The mechanisms of action of essential oils and total plant extracts against mosquito larvae are multifaceted and distinct. Essential oils primarily exert their larvicidal effects through contact toxicity, neurotoxicity, and enzyme inhibition. Upon contact, essential oils disrupt the larvae’s cuticle, leading to desiccation and death. Neurotoxic components, such as monoterpenes and sesquiterpenes, interfere with the nervous system, causing paralysis and mortality. Additionally, some essential oils inhibit acetylcholinesterase, an enzyme crucial for nerve signal transmission, further disrupting larval neural functions. In contrast, total plant extracts, which encompass a broader range of bioactive compounds, act through multiple mechanisms including growth disruption, metabolic inhibition, and oviposition deterrence. The diverse chemical constituents in plant extracts, such as alkaloids, flavonoids, and saponins, interfere with larval development and molting processes, disrupt energy metabolism, and deter female mosquitoes from laying eggs in treated water. These combined actions make both essential oils and plant extracts effective larvicides, though their specific mechanisms and applications may vary depending on the plant species and extraction methods used 97 , 98 , 99 , 100 .
Botanically derived natural larvicides are gaining attention as safety and environmentally friendly alternatives to synthetic insecticides for mosquito control. Despite their benefits, such as lower chemical residues and reduced toxicity to non-target organisms, there are still potential environmental impacts and safety concerns that must be considered. Additionally, the persistence and degradation of these natural compounds in the environment are not always well understood. While the safety profile of natural larvicides for humans and animals is generally better than that of synthetic insecticides, some natural compounds can still pose risks. Furthermore, the variability in the composition of natural extracts can lead to inconsistent efficacy and safety profiles. Standardization and rigorous testing are essential to ensure the safe use of these products 101 , 102 , 103 .
Our study offers encouraging indications of the larvicidal potential of D. speciosum extract and T. ammi EO. However, it’s crucial to recognize some limitations. The experiments were carried out in a controlled laboratory environment. To evaluate the effectiveness and practicality of these plant-derived compounds in real-world vector control programs, additional field-based assessments are required. Furthermore, identifying and characterizing the specific phytochemicals that contribute to the observed larvicidal activities calls for more in-depth investigation.
Our study has highlighted the substantial larvicidal effects of D. speciosum extract and T. ammi EO against three primary disease vector mosquitoes. The larvicidal activity of T. ammi essential oil surpasses that of D. speciosum extract, with the optimal concentration being 40 ppm. Additionally, among the species studied, Cx. quinquefasciatus exhibits the highest sensitivity to these plant-derived treatments. Thymol is the main component of T. ammi EO, and the alkaloids in D. speciosum extract have diterpene structures. Considering the effect size values, along with the dose-dependent trends and species-specific responses can help researchers gain a more comprehensive understanding of the real-world implications and potential utility of the plant-derived larvicides investigated in this study. Future studies should include both laboratory and field trials to evaluate their effectiveness against diverse mosquito populations, assess its environmental impact, and determine optimal application methods for their practical use in vector control.
Data availability
The datasets used and/or analysed during the current study available from the corresponding author on reasonable request.
Reinhold, J. M., Lazzari, C. R. & Lahondère, C. Effects of the environmental temperature on Aedes aegypti and Aedes albopictus mosquitoes: A review. Insects 9 , 158 (2018).
Article PubMed PubMed Central Google Scholar
Gabrieli, P., Smidler, A. & Catteruccia, F. Engineering the control of mosquito-borne infectious diseases. Genome Biol. 15 , 1–9 (2014).
Article Google Scholar
CDC. Centers for Disease Control and Prevention. Where mosquitoes live 2024. https://www.cdc.gov/mosquitoes/about/where-mosquitoes-live_1.html . (accessed 22 June 2024).
Wilder-Smith, A. et al. Epidemic arboviral diseases: Priorities for research and public health. Lancet Infect. Dis. 17 , e101–e106 (2017).
Article PubMed Google Scholar
Benelli, G. & Mehlhorn, H. Declining malaria, rising of dengue and Zika virus: insights for mosquito vector control. Parasitol. Res. 115 , 1747–1754 (2016).
Benelli, G. Research in mosquito control: Current challenges for a brighter future. Parasitol. Res. 114 , 2801–2805 (2015).
Samy, A. M. et al. Climate change influences on the global potential distribution of the mosquito Culex quinquefasciatus , vector of West Nile virus and lymphatic filariasis. PLoS ONE 11 , e0163863 (2016).
Benelli, G. et al. Acute larvicidal toxicity of five essential oils ( Pinus nigra , Hyssopus officinalis , Satureja montana , Aloysia citrodora and Pelargonium graveolens ) against the filariasis vector Culex quinquefasciatus : Synergistic and antagonistic effects. Parasitol. Int. 66 , 166–171 (2017).
Article CAS PubMed Google Scholar
Thandapani, K. et al. Enhanced larvicidal, antibacterial, and photocatalytic efficacy of TiO 2 nanohybrids green synthesized using the aqueous leaf extract of Parthenium hysterophorus . Environ. Sci. Pollut. Res. 25 , 10328–10339 (2018).
Article CAS Google Scholar
WHO. World Health Organisation. lymphatic philariasis key facts 2023 https://www.who.int/news-room/fact-sheets/detail/lymphatic-filariasis . (accessed 1 June 2023).
Liu, Q. et al. Possible potential spread of Anopheles stephensi , the Asian malaria vector. BMC Infect. Dis. 24 , 333 (2024).
WHO. World Health Organisation. Malaria key facts 2023 https://www.who.int/news-room/fact-sheets/detail/malaria . (accessed 4 December 2023).
Brady, O. J. et al. Refining the global spatial limits of dengue virus transmission by evidence-based consensus. PLoS Negl. Trop. Dis. 6 , e1760 (2012).
WHO. World Health Organisation. Dengue and severe dengue https://www.who.int/news-room/fact-sheets/detail/dengue-and-severe-dengue . (accessed 17 March 2023).
Laith, A. E., Alnimri, M., Ali, H., Alkhawaldeh, M. & Mihyar, A. Mosquito-borne diseases: assessing risk and strategies to control their spread in the Middle East. J. Biosaf. Biosecur. 6 , 1–12 (2024).
Floore, T. G. Mosquito larval control practices: Past and present. J. Am. Mosq. Control Assoc. 22 , 527–533 (2006).
Naqqash, M. N., Gökçe, A., Bakhsh, A. & Salim, M. Insecticide resistance and its molecular basis in urban insect pests. Parasitol. Res. 115 , 1363–1373 (2016).
Mansouri, A. et al. The environmental issues of DDT pollution and bioremediation: A multidisciplinary review. Appl. Biochem. Biotechnol. 181 , 309–339 (2017).
Serrão, J. E., Plata-Rueda, A., Martínez, L. C. & Zanuncio, J. C. Side-effects of pesticides on non-target insects in agriculture: A mini-review. Sci. Nat. 109 , 17 (2022).
Selvakumaran, J. et al. Evaluation of mosquitocidal, histopathological and non-target effect of botanical pesticides from Stemodia viscosa and their mixtures against immature stages of Aedes aegypti, Anopheles stephensi and Culex quinquefasciatus . . Biologia 79 , 1425–1437 (2024).
Khater, H. F. Prospects of botanical biopesticides in insect pest management. Pharmacologia 3 , 641–656 (2012).
Govindarajan, M., Rajeswary, M. & Benelli, G. Chemical composition, toxicity and non-target effects of Pinus kesiya essential oil: An eco-friendly and novel larvicide against malaria, dengue and lymphatic filariasis mosquito vectors. Ecotoxicol. Environ. Saf. 129 , 85–90 (2016).
Nenaah, G. E. & Ibrahim, S. I. Chemical composition and the insecticidal activity of certain plants applied as powders and essential oils against two stored-products coleopteran beetles. J. Pest Sci. 84 , 393–402 (2011).
Sousa, Z. L. et al. Biological activities of extracts from Chenopodium ambrosioides Lineu and Kielmeyera neglecta Saddi . Ann. Clin. Microbiol. Antimicrob. 11 , 1–7 (2012).
Article ADS Google Scholar
Pavela, R. et al. Clausena anisata and Dysphania ambrosioides essential oils: From ethno-medicine to modern uses as effective insecticides. Environ. Sci. Pollut. Res. 25 , 10493–10503 (2018).
Kavallieratos, N. G. et al. Effectiveness of eight essential oils against two key stored-product beetles, Prostephanus truncatus (Horn) and Trogoderma granarium everts. Food Chem. Toxicol. 139 , 111255 (2020).
Haddi, K. et al. Rethinking biorational insecticides for pest management: Unintended effects and consequences. Pest Manag. Sci. 76 , 2286–2293 (2020).
Article ADS CAS PubMed Google Scholar
Dai, D. N. et al. Chemical compositions, mosquito larvicidal and antimicrobial activities of essential oils from five species of cinnamomum growing wild in north central Vietnam. Molecules 25 , 1303 (2020).
Article CAS PubMed PubMed Central Google Scholar
Eden, W. T., Alighiri, D., Supardi, K. I. & Cahyono, E. The mosquito repellent activity of the active component of air freshener gel from java citronella oil ( Cymbopogon winterianus ). J. Parasitol. Res. 202 , 1–5 (2020).
Silvério, M. R. S., Espindola, L. S., Lopes, N. P. & Vieira, P. C. Plant natural products for the control of Aedes aegypti : The main vector of important arboviruses. Molecules 25 , 3484 (2020).
Vasudevan, P., Kashyap, S. & Sharma, S. Tagetes: A multipurpose plant. Bioresour. Technol. 62 , 29–35 (1997).
Ansari, M., Vasudevan, P., Tandon, M. & Razdan, R. Larvicidal and mosquito repellent action of peppermint ( Mentha piperita ) oil. Bioresour. Technol. 71 , 267–271 (2000).
Sanei-Dehkordi, A., Moemenbellah-Fard, M. D., Saffari, M., Zarenezhad, E. & Osanloo, M. Nanoliposomes containing limonene and limonene-rich essential oils as novel larvicides against malaria and filariasis mosquito vectors. BMC Complement. Med. Ther. 22 , 140 (2022).
Benelli, G. et al. Carlina acaulis and Trachyspermum ammi essential oils formulated in protein baits are highly toxic and reduce aggressiveness in the medfly Ceratitis capitata . Ind. Crops Prod. 161 , 113191 (2021).
Sen-Utsukarci, B. et al. The cytotoxicity and insecticidal activity of extracts from Delphinium formosum boiss. & huet. Istanb. J. Pharm. 49 , 148–153 (2019).
Google Scholar
Pitarokili, D., Michaelakis, A., Koliopoulos, G., Giatropoulos, A. & Tzakou, O. Chemical composition, larvicidal evaluation, and adult repellency of endemic Greek Thymus essential oils against the mosquito vector of West Nile virus. Parasitol. Res. 109 , 425–430 (2011).
Michaelakis, A., Theotokatos, S. A., Koliopoulos, G. & Chorianopoulos, N. G. Essential oils of Satureja species: insecticidal effect on Culex pipiens larvae ( Diptera : Culicidae ). Molecules 12 , 2567–2578 (2007).
Tabari, M. A., Youssefi, M. R., Esfandiari, A. & Benelli, G. Toxicity of β-citronellol, geraniol and linalool from Pelargonium roseum essential oil against the West Nile and filariasis vector Culex pipiens ( Diptera : Culicidae ). Res. Vet. Sci. 114 , 36–40 (2017).
Al-Mekhlafi, F. A. Larvicidal, ovicidal activities and histopathological alterations induced by Carum copticum ( Apiaceae ) extract against Culex pipiens ( Diptera : Culicidae ). Saudi J. Biol. Sci. 25 , 52–56 (2018).
Andrade-Ochoa, S. et al. Oviposition deterrent and larvicidal and pupaecidal activity of seven essential oils and their major components against Culex quinquefasciatus Say ( Diptera : Culicidae ): synergism–antagonism effects. Insects 9 , 25 (2018).
Pandey, S., Upadhyay, S. & Tripathi, A. Insecticidal and repellent activities of thymol from the essential oil of Trachyspermum ammi (Linn) sprague seeds against Anopheles stephensi . Parasitol. Res. 105 , 507–512 (2009).
Kadam, S. S., More, S. B. & Waghmare, J. S. Tranchyspermum Ammi : Natural pesticides. J. Biopest. 10 , 90–98 (2017).
Bhadra, P. An overview of Ajwain ( Trachyspermum ammi ). Indian J. Nat. Sci. 10 , 18466–182474 (2020).
Gheybi, S., Asnaashari, S., Moghaddam, S. B., Ebrahimi, A. & Afshar, F. H. Volatile components of aerial parts of Delphinium speciosum MB growing in Iran. J. Rep. Pharm. Sci. 4 , 191–195 (2015).
Vicentini, C. B., Manfredini, S. & Contini, C. Ancient treatment for lice: A source of suggestions for carriers of other infectious diseases?. Infez. Med. 26 , 181–192 (2018).
PubMed Google Scholar
Shan, L., Chen, L., Gao, F. & Zhou, X. Diterpenoid alkaloids from Delphinium naviculare var. lasiocarpum with their antifeedant activity on Spodoptera exigua . Nat. Prod. Res. 33 , 3254–3259 (2019).
Suresh, G. et al. Green synthesis of silver nanoparticles using Delphinium denudatum root extract exhibits antibacterial and mosquito larvicidal activities. Spectrochim. Acta Part A Mol. Biomol. Spectrosc. 127 , 61–66 (2014).
Article ADS CAS Google Scholar
Dey, P. et al. Recent Advances in Natural Products Analysis (Elsevier, 2020).
Pereira, A. G. et al. Natural Secondary Metabolites: From Nature, Through Science, to Industry (Springer, 2023).
Kumar, A., Shukla, R., Singh, P. & Dubey, N. K. Chemical composition, antifungal and antiaflatoxigenic activities of Ocimum sanctum L. essential oil and its safety assessment as plant based antimicrobial. Food Chem. Toxicol. 48 , 539–543 (2010).
WHO. World Health Organization. Guidelines for laboratory and field testing of mosquito larvicides (No. WHO/CDS/WHOPES/GCDPP/2005.13).
Bahadori, M. B., Asnaashari, S. & Nazemiyeh, H. Fatty acid profile of roots and aerial parts of Ruscus hyrcanus Woronow. Pharma. Sci. 25 , 78–81 (2019).
Wei, Y. et al. 1H NMR guided isolation of 3-arylisoquinoline alkaloids from Hypecoum erectum L. and their anti-inflammation activity. Phytochemistry 222 , 114093 (2024).
Xiao, J. et al. 1H NMR-guided isolation of hasubanan alkaloids from the alkaloidal extract of Stephania longa . Bioorg. Chem. 139 , 106717 (2023).
Zhao, C.-X. et al. 1H-NMR-guided isolation of enantiomeric coumarin-monoterpenes with anti-inflammatory activity from Gerbera piloselloides . Phytochemistry 203 , 113346 (2022).
Wang, A. D. et al. Isolation and structure determination of new saponins from Pulsatilla cernua based on an NMR-guided method and their anti-proliferative activities. Phytochem. Lett. 27 , 9–14 (2018).
Zhang, Y. et al. Isolation of a new monoterpenoid glycoside from anhua dark tea based on an NMR-guided method and its cytotoxic activity against MDA-MB-231 and SH-SY5Y cell lines. Nat. Prod. Res. 36 , 2015–2020 (2022).
Elliott, A. C. & Woodward, W. A. Statistical Analysis Quick Reference Guidebook: with SPSS Examples (Sage, 2007).
Book Google Scholar
Cohen, J. Statistical Power Analysis for the Behavioral Sciences (Routledge, 2013).
Rahimi, S., Vatandoost, H., Abai, M. R., Raeisi, A. & Hanafi-Bojd, A. A. Status of resistant and knockdown of West Nile vector, Culex pipiens complex to different pesticides in Iran. J. Arthropod Borne Dis. 13 , 284 (2019).
PubMed PubMed Central Google Scholar
Rahimi, S. et al. Resistant status of Culex pipiens complex species to different imagicides in Tehran Iran. J.Vect. Borne Dis. 57 , 47–51 (2020).
González-Coloma, A. et al. Antifeedant delphinium diterpenoid alkaloids. Structure—Activity relationships. J. Agric. Food Chem. 46 , 286–290 (1998).
Miles, J. E., Ramsewak, R. S. & Nair, M. G. Antifeedant and mosquitocidal compounds from delphinium× cultorum Cv. magic fountains flowers. J. Agric. Food Chem. 48 , 503–506 (2000).
Ulubelen, A. et al. Insect repellent activity of diterpenoid alkaloids. Phytother. Res. 15 , 170–171 (2001).
Ramírez-Macías, I. et al. Leishmanicidal activity of nine novel flavonoids from Delphinium staphisagria . Sci. World J. 2012 , 203646 (2012).
Yan, Y., Li, X., Wang, Z., Yang, X. & Yin, T. C 18-diterpenoid alkaloids in tribe Delphineae ( Ranunculaceae ): Phytochemistry, chemotaxonomy, and bioactivities. RSC Adv. 12 , 395–405 (2022).
Vicentini, C. B., Manfredini, S. & Contini, C. Ancient treatment for lice: A source of suggestions for carriers of other infectious diseases?. Le Infez. Med. 26 , 181–192 (2018).
Alghamdi, A. A. & Basher, N. S. Efficacy of leaves and flowers ethanol extracts of the invasive species Lantana camara Linn as a mosquito larvicidal. Int. J. Mosq. Res. 7 , 43–47 (2020).
Fasasi, K., Olawoyin, M. O., Rufai, A. M. & Iwalewa, Z. O. Anales de Biología (Servicio de Publicaciones de la Universidad de Murcia, 2024).
Mandal, P. & Chandra, G. Casearia tomentosa fruit extracts exposed larvicidal activity and morphological alterations in Culex q uinquefasciatus and Aedes albopictus under in vitro and semi field conditions. BMC Res. Notes 17 , 6 (2024).
Pirmohammadi, M. et al. Influence of agro-climatic conditions on chemical compositions and repellency effect of Mentha longifolia plant against malaria vector Anopheles stephensi . Toxin Rev. 42 , 115–121 (2023).
Baz, M. M., Selim, A., Radwan, I. T., Alkhaibari, A. M. & Khater, H. F. Larvicidal and adulticidal effects of some Egyptian oils against Culex pipiens . Sci. Rep. 12 , 4406 (2022).
Article ADS CAS PubMed PubMed Central Google Scholar
Bisrat, D. & Jung, C. Insecticidal toxicities of three main constituents derived from T rachyspermum ammi (L.) Sprague ex turrill fruits against the small hive beetles, Aethina tumida murray. Molecules 25 , 1100 (2020).
Seo, S. M., Park, H. M. & Park, I. K. Larvicidal activity of ajowan ( Trachyspermum ammi ) and Peru balsam ( Myroxylon pereira ) oils and blends of their constituents against mosquito, Aedes aegypti , acute toxicity on water flea, Daphnia magna , and aqueous residue. J. Agric. Food Chem. 60 , 5909–5914 (2012).
Kusman, I. T. et al. The potentials of Ageratum conyzoides and other plants from Asteraceae as an antiplasmodial and insecticidal for malaria vector: An article review. Infect. Drug Resist. 16 , 7109–7138 (2023).
Ammar, S. et al. Essential oils from three Algerian medicinal plants ( Artemisia campestris , Pulicaria arabica , and Saccocalyx satureioides ) as new botanical insecticides?. Environ. Sci. Pollut. Res. 27 , 26594–26604 (2020).
Benelli, G. et al. Ascaridole-rich essential oil from marsh rosemary ( Ledum palustre ) growing in Poland exerts insecticidal activity on mosquitoes, moths and flies without serious effects on non-target organisms and human cells. Food Chem. Toxicol. 138 , 111184 (2020).
Žabka, M. et al. Antifungal and insecticidal potential of the essential oil from Ocimum sanctum L. against dangerous fungal and insect species and its safety for non-target useful soil species Eisenia fetida (Savigny, 1826). Plants 10 , 2180 (2021).
Huong, L. T. et al. Essential oils of Zingiber species from Vietnam: Chemical compositions and biological activities. Plants 9 , 1269 (2020).
An, N. T. G. et al. Mosquito larvicidal activity, antimicrobial activity, and chemical compositions of essential oils from four species of Myrtaceae from central Vietnam. Plants 9 , 544 (2020).
Inaba, K. et al. Molecular action of larvicidal flavonoids on ecdysteroidogenic glutathione S-transferase Noppera-bo in Aedes aegypti . BMC Biol. 20 , 43 (2022).
Antonio-Nkondjio, C., Sandjo, N. N., Awono-Ambene, P. & Wondji, C. S. Implementing a larviciding efficacy or effectiveness control intervention against malaria vectors: Key parameters for success. Parasites Vect. 11 , 1–12 (2018).
García-Díaz, J. et al. Larvicidal and adulticidal activity of essential oils from four cuban plants against three mosquito vector species. Plants 12 , 4009 (2023).
Chaves, R. D. S. B. et al. Evaluation of larvicidal potential against larvae of Aedes aegypti ( Linnaeus , 1762) and of the antimicrobial activity of essential oil obtained from the leaves of Origanum majorana L.. PLoS ONE 15 , e0235740 (2020).
Kiran, S. R., Bhavani, K., Devi, P. S., Rao, B. R. & Reddy, K. J. Composition and larvicidal activity of leaves and stem essential oils of Chloroxylon swietenia DC against Aedes aegypti and Anopheles stephensi . Bioresour. Technol. 97 , 2481–2484 (2006).
Nguta, J. et al. Biological screening of Kenya medicinal plants using Artemia salina L. ( Artemiidae ). Pharmacologyonline 2 , 458–478 (2011).
Chaubey, M. K. Insecticidal activity of Trachyspermum ammi ( Umbelliferae ), Anethum graveolens (Umbelliferae) and Nigella sativa ( Ranunculaceae ) essential oils against stored-product beetle Tribolium castaneum herbst ( Coleoptera : Tenebrionidae ). Afr. J. Agric. Res. 2 , 596–600 (2007).
Sahaf, B. Z., Moharramipour, S. & Meshkatalsadat, M. H. Chemical constituents and fumigant toxicity of essential oil from Carum copticum against two stored product beetles. Insect Sci. 14 , 213–218 (2007).
Moein, M. R. et al. Trachyspermum ammi (L.) sprague: Chemical composition of essential oil and antimicrobial activities of respective fractions. J. Evid. Based Complement. Altern. Med. 20 , 50–56 (2015).
Rasooli, I. et al. Antimycotoxigenic characteristics of Rosmarinus officinalis and Trachyspermum copticum L. essential oils. Int. J. Food Microbiol. 122 , 135–139 (2008).
Khajeh, M., Yamini, Y., Sefidkon, F. & Bahramifar, N. Comparison of essential oil composition of Carum copticum obtained by supercritical carbon dioxide extraction and hydrodistillation methods. Food Chem. 86 , 587–591 (2004).
Srivastava, M., Baby, P. & Saxena, A. GC-MS investigation and antimicrobial activity of the essential oil of Carum c opticum benth & hook. Acta Aliment. 28 , 291–295 (1999).
Mohagheghzadeh, A., Faridi, P. & Ghasemi, Y. Carum copticum Benth & Hook essential oil chemotypes. Food Chem. 100 , 1217–1219 (2007).
Shojaaddini, M., Moharramipour, S. & Sahaf, B. Fumigant toxicity of essential oil from Carum copticum against Indian meal moth, Plodia interpunctella . J. Plant Protect. Res. https://doi.org/10.2478/v10045-008-0050-5 (2008).
Dhaiwal, K., Chahal, K. K., Kataria, D. & Kumar, A. Gas chromatography-mass spectrometry analysis and in vitro antioxidant potential of ajwain seed ( Trachyspermum ammi L.) essential oil and its extracts. J. Food Biochem. 41 , e12364 (2017).
Lotfaliani, M., Ayatollahi, S. A., Kobarfard, F. & Pour, P. M. Chemistry, biological activities and toxic effects of alkaloidal constituents of genus Delphinium —A mini review. J. Herbmed. Pharmacol. 10 , 486–499 (2021).
Kelly, P. H., Yingling, A. V., Ahmed, A., Hurwitz, I. & Ramalho-Ortigao, M. Defining the mechanisms of action and mosquito larva midgut response to a yeast-encapsulated orange oil larvicide. Parasites Vect. 15 , 183 (2022).
Cruz-Castillo, A. U. et al. Terpenic constituents of essential oils with larvicidal activity against Aedes Aegypti : A QSAR and docking molecular study. Molecules 28 , 2454 (2023).
Isman, M. B. & Tak, J. H. Inhibition of acetylcholinesterase by essential oils and monoterpenoids: a relevant mode of action for insecticidal essential oils? Biopest. Int. 13 , 71–78 (2017).
Pavela, R., Maggi, F., Iannarelli, R. & Benelli, G. Plant extracts for developing mosquito larvicides: From laboratory to the field, with insights on the modes of action. Acta Tropica 193 , 236–271 (2019).
Pavela, R. & Benelli, G. Essential oils as ecofriendly biopesticides? Challenges and constraints. Trends Plant Sci. 21 , 1000–1007 (2016).
Nawaz, M., Mabubu, J. I. & Hua, H. Current status and advancement of biopesticides: Microbial and botanical pesticides. J. Entomol. Zool. Stud. 4 , 241–246 (2016).
Mathew, L. K. Botanicals as biopesticides: A review. Int. J. Adv. Res. 4 , 1734–1739 (2016).
CAS Google Scholar
Download references
Acknowledgements
Our appreciation goes to Dr. A.A. Keshtkar, Dr. A. Latifi, Dr. A. Ebrahimi, and Mr. A. Azadnia for his direction and counsel throughout the project.
This work was founded and supported by the Maragheh University of Medical Sciences (MRGUMS), (IR.MARAGHEHPHC.REC.1401.012) Maragheh, Iran.
Author information
These authors contributed equally: Sara Rahimi and Hossein Nazemiyeh.
Authors and Affiliations
Infectious and Tropical Diseases Research Center, Hormozgan Health Institute, Hormozgan University of Medical Sciences, Bandar Abbas, Iran
Alireza Sanei‑Dehkordi
Student Research Committee, Faculty of Pharmacy, Tabriz University of Medical Sciences, Tabriz, Iran
Amir Masoud Tagizadeh
Medicinal Plants Research Center, Maragheh University of Medical Sciences, Maragheh, Iran
Mir Babak Bahadori, Elhameh Nikkhah & Sara Rahimi
Department of Vector Biology and Control of Diseases, School of Public Health, Tehran University of Medical Sciences, Tehran, Iran
Masoumeh Pirmohammadi
Department of Pharmacognosy, Faculty of Pharmacy, Tabriz University of Medical Sciences, Tabriz, Iran
Hossein Nazemiyeh
You can also search for this author in PubMed Google Scholar
Contributions
Conceptualization, S.R., H.N., and A.S-D.; Methodology, H.N., M.P., and A.S-D.; Formal Analysis, S.R., and M-B.B.; Investigation, S.R., A-M.T., and H.N.; Data Curation, S.R., E.N., and M-B.B.; Writing—Original Draft Preparation, S.R., A.S-D., M-B.B., and A-M.T.; Writing—Review & Editing, S.R., H.N., A.S-D., M-B.B., A-M.T., E.N., and M.P.; Supervision, H.N.; Project Administration, S.R.; All authors have read and agreed to the published version of the manuscript.
Corresponding authors
Correspondence to Sara Rahimi or Hossein Nazemiyeh .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Cite this article.
Sanei‑Dehkordi, A., Tagizadeh, A.M., Bahadori, M.B. et al. Larvicidal potential of Trachyspermum ammi essential oil and Delphinium speciosum extract against malaria, dengue, and filariasis mosquito vectors. Sci Rep 14 , 20677 (2024). https://doi.org/10.1038/s41598-024-71829-x
Download citation
Received : 11 July 2024
Accepted : 30 August 2024
Published : 05 September 2024
DOI : https://doi.org/10.1038/s41598-024-71829-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Larvicidal activity
- Culex quinquefasciatus
- Aedes aegypti
- Anopheles stephensi
- Essential oil
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: Translational Research newsletter — top stories in biotechnology, drug discovery and pharma.

IMAGES
VIDEO
COMMENTS
The critical incident technique (CIT) is a qualitative research tool that is frequently used in health services research to explore what helps or hinders in providing good quality care or achieving satisfaction with care provision. However, confusion currently exists on the nature of the CIT: Is it a method for data collection and analysis or a ...
The critical incident technique (CIT) is a qualitative research tool that is frequently used in health services research to explore what helps or hinders in providing good quality care or achieving satisfaction with care provision. However, confusion currently exists on the nature of the CIT: Is it a method for data collection and analysis or a methodology? In this article, I explain why this ...
The critical incident technique is a qualitative research method that involves analyzing and interpreting specific events or incidents to understand how individuals respond. This approach involves ...
It has now been 50 years since Flanagan (1954) published his classic article on the critical incident technique (CIT) - a qualitative research method that is still widely used today. This article r...
It is argued that the critical incident technique is a methodology (and not a method) for the following reasons: Key methodological dimensions are described for the CIT; it has a clear focus and it implies philosophical and practical assumptions. The critical incident technique (CIT) is a qualitative research tool that is frequently used in health services research to explore what helps or ...
The Critical Incident Technique (CIT), a research method that relies on a set of procedures to collect, content analyze, and classify observations of human behavior, was introduced to the social sciences by Flanagan (1954) 60 years ago. Bitner, Booms, and Tetreault (1990), who introduced CIT to the marketing discipline, define an incident as an ...
The critical incident technique (CIT) is a qualitative research tool that is frequently used in health services research to explore what helps or hinders in providing good quality care or achieving satisfaction with care provision. However, confusion currently exists on the nature of the CIT: Is it a method for data collection and analysis or a methodology?
The critical incident technique (CIT) is a qualitative research method that is used to. obtain a depth of knowledge and understanding of subjects' responses to selected. situations. The method ...
The critical incident technique (or CIT) is a set of procedures used for collecting direct observations of human behavior that have critical significance and meet methodically defined criteria. These observations are then kept track of as incidents, which are then used to solve practical problems and develop broad psychological principles. A critical incident can be described as one that makes ...
The Critical Incident Technique
† The Critical Incident technique helps identify and analyze rare events or cir-cumstances that might not be picked up by methods of investigation dealing with everyday episodes. Its focus on critical issues can bring major benefits. † The Critical Incident technique maximizes the positive and minimizes the
This entry describes the Critical Incident Technique (CIT), which is a powerful qualitative research method that generates insightful narrative data about user experiences with specific programs and services. The key steps in conducting and reporting CIT are described, as are the uses and applications of CIT data. The data gathered with CIT ...
of this method-launching article, he acknowledged in the publication that a number of collaborators and graduate students conducted similar studies as he developed the method, utilizing a critical incident approach to identify "the critical requirements" (pp. 5-6) in a variety of other professions including:
• The Critical Incident technique helps identify and analyze rare events or circumstances that might not be picked up by methods of investigation dealing with everyday episodes. Its focus on critical issues can bring major benefits. • The Critical Incident technique maximizes the positive and minimizes the negative attributes of anecdotes,
The critical incident technique (CIT) is a research method in which the research participant is asked to recall and describe a time when a behavior, action, or occurrence impacted (either positively or negatively) a specified outcome (for example, the accomplishment of a given task). The instance reported by the participant is known as an ...
Abstract. Critical Incident Technique (CIT) is a method that defines a set of procedures to investigate what positively or negatively affects an experience or activity. It originated as a quantitative approach to combat problems encountered by the U.S. Army Air Forces during the Second World War.
The critical incident technique is an exploratory qualitative method of research that has been shown both reliable and valid in generating a comprehensive and detailed description of a content domain. After being used widely in industrial psychology during the 1950's, the technique fell into diverse and is only now enjoying a renaissance. The critical incident technique basically consists of ...
Critical incident method or critical incident technique is a performance appraisal tool in which analyses the behavior of employee in certain events in which either he performed very well and the ones in which he could have done better. Critical incident technique is used to collect data using a set of procedures. In critical incident method the observer observes critical human behaviors ...
Critical incident technique like all methods has some advantages and disadvantages. The advantages can be listed as. If Critical Incident Technique is used, it reveals the errors and issues fast. There is no timeframe for taking incidents. The participant can take how much time he wants to evaluate and answer questions.
The critical incident technique is a five-stage process that has the following steps. 1. Establish aims. The first stage establishes the aims of the activity. It lays down the groundwork that will determine what comes under the critical incident. This step involves identifying and reviewing the incidents that have occurred during the job.
The critical incident technique, is a highly flexible qualitative research method used in solving practical problems and offers the following important advantages to those interested in designing studies of care quality: identifying patients' experiences in health care settings, exploring dimensions of nurse-patient interactions and identifies ...
Objectives The purpose of this study was to describe the experiences and actions of part-time firefighters' family members in rural areas in Sweden. Design The study had an inductive descriptive design and used the critical incident technique. Setting Rural areas, primarily served by a part-time fire station, across Sweden. Participants The study included 25 participants (21 females and 4 ...
Triage methods streamline operations by swiftly matching appropriate resources with specific tasks at the optimal moment. This guarantees that skilled professionals will promptly address critical incidents. ... Analysts may employ various tools and techniques, such as timeline analysis, log correlation, and malware sandboxing, to piece together ...
Tool wear management and real-time machining quality monitoring are pivotal components of realizing smart manufacturing objectives, as they directly influence machining precision and productivity. Traditionally, measuring and analyzing cutting force fluctuations in the time domain has been employed to diagnose tool wear effects. This study introduces a novel, indirect approach that leverages ...
It should be noted that the NMR guided isolation method is a valuable technique that has been widely used by researchers in metabolomic studies and drug discovery.